Featured posts

Akamai Technologies has announced a series of new products and updates to existing products across its security and compute product…
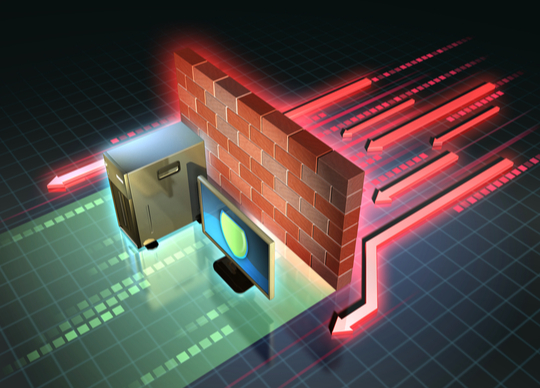
Sophos has introduced a new version of Sophos Firewall with Xstream software-defined wide area network (SD-WAN) capabilities and virtual private…

By Unit 42, Palo Alto Networks. The ongoing transition to cloud platforms has meant that more sensitive data is stored…

ForgeRock has announced the availability of its next-generation Authenticator App. The redesigned app offers a quicker and simpler login process…

Red Piranha has announced Nicola Nicol and David Plisek will join their Corporate Advisory Panel. Nicola is an experienced consultant…

By Staff Writer. The Five Eyes countries have joined forces to warn of likely Russian State sponsored and criminal cyber-threats…

By Wayne Arvidson, Global Director, Market Development and Strategy, Dell Technologies | APR 12, 2022 7:33 AM PDT Computer vision is…

According to the latest data from the ACCC’s Scamwatch statistics, Australians lost a staggering $95 million to all types of scams…

ESET researchers have discovered and analyzed three vulnerabilities affecting various Lenovo consumer laptop models. The exploitation of these vulnerabilities would…

By Chris Cubbage CISA, Editor. Despite a delay due to border closures, the inaugural South Australian Cyber Risk Meetup was…

