Precisely one year after the SolarWinds Hack, the groundbreaking supply chain attack the world experienced, and while organisations are still struggling to protect the software supply chain from third-party risk, the Apache Log4j vulnerability exploit has caught security teams during a weekend.
Unlike other major cyber-attacks that involve one or a limited number of software, Log4j is basically embedded in every Java based product or web service. It is very difficult to manually remediate it. Once an exploration was published (on Friday), scans of the internet ensued (to allocate surfaces which are vulnerable due to this incident). Those who won’t implement a protection are probably already scanned by malicious actors.
Since Friday, December 9th, when the vulnerability was reported, actors around the world are on the lookout for exploits. The number of combinations of how to exploit it give the attacker many alternatives to bypass newly introduced protections. It means that one layer of protection is not enough, and only multi-layered security posture would provide a resilient protection. Three days after the outbreak, we are summing up what we see until now, which is clearly a cyber pandemic that hasn’t seen its peak yet.
A TRUE CYBER – PANDEMIC
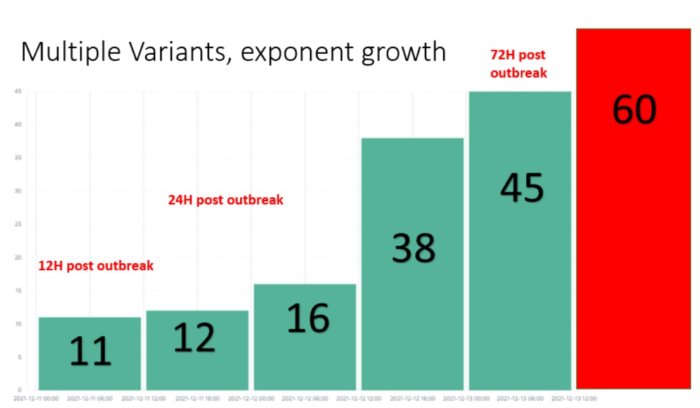
Diving into the numbers behind the attack, gathered and analysed by Check Point Research, we see a pandemic-like spread since the outbreak on Friday, by the beginning of the week, on Monday.
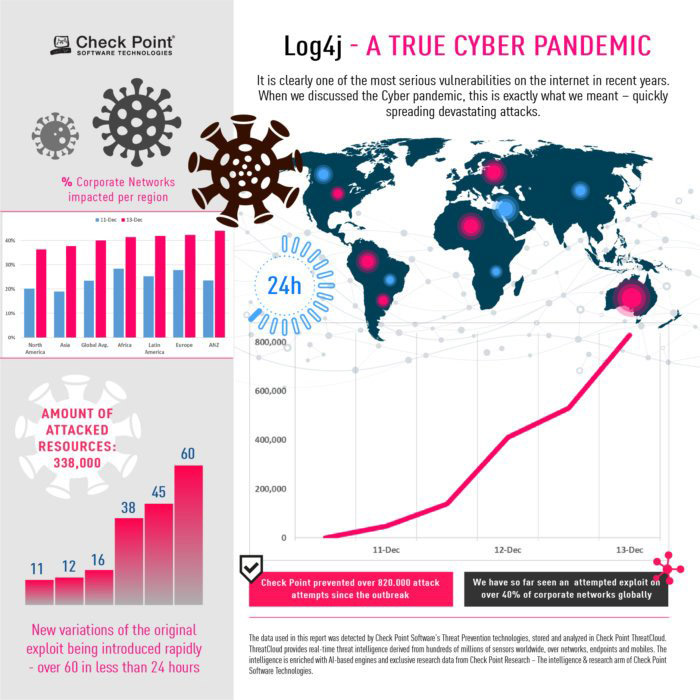
Early reports on December 10th showed merely thousands of attack attempts, rising to over 40,000 during Saturday, December 11th. Twenty-four hours after the initial outbreak our sensors recorded almost 200,000 attempts of attack across the globe, leveraging this vulnerability. As of the time these lines are written, 72 hours post initial outbreak, the number hit over 800,000 attacks.
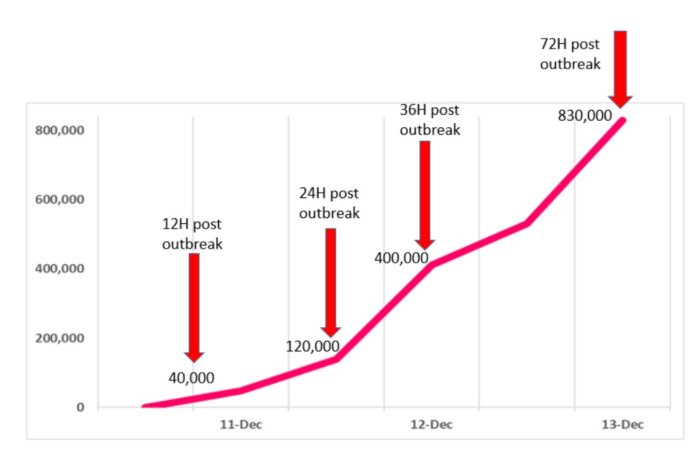
It is clearly one of the most serious vulnerabilities on the internet in recent years, and the potential for damage is incalculable. Check Point Research witnessed new variations of the original exploit being introduced rapidly- over 60 in less than 24 hours.
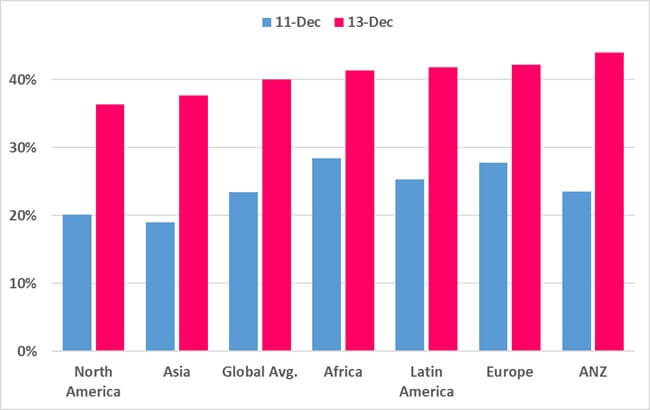
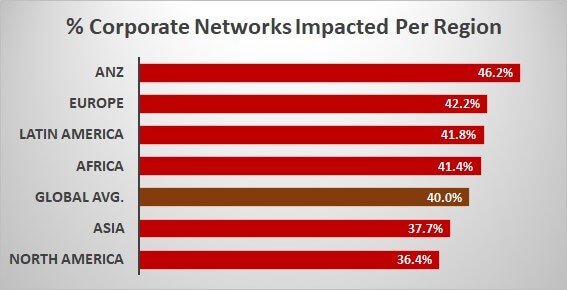
CORPORATE NETWORKS IMPACTED GLOBALLY
One of the most dramatic characteristics of a cyber pandemic are major vulnerabilities in popular software and services, which impact an enormous number of organisations across the globe, spreading like wild fire.
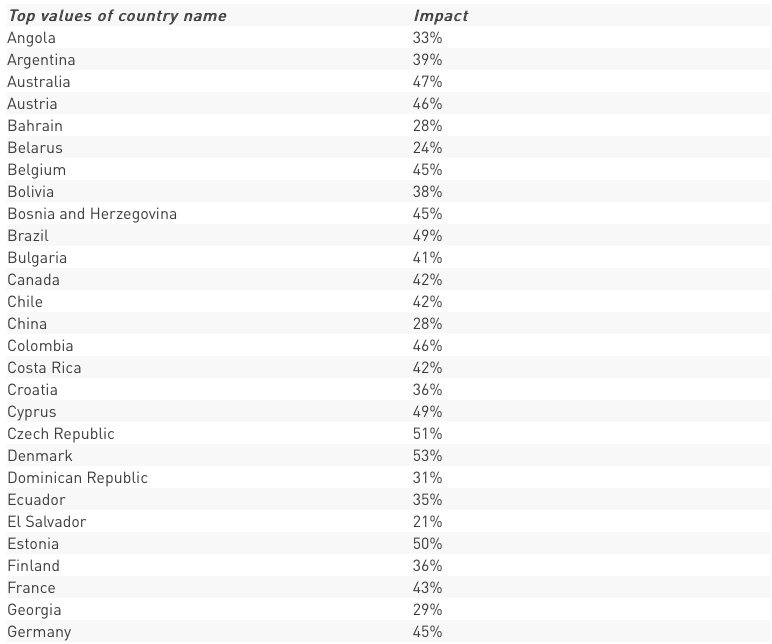
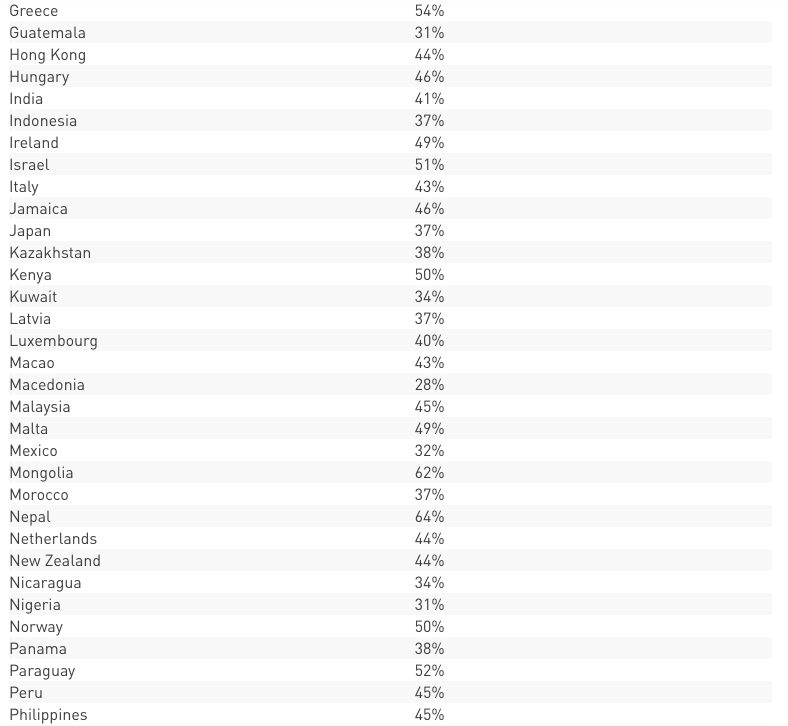
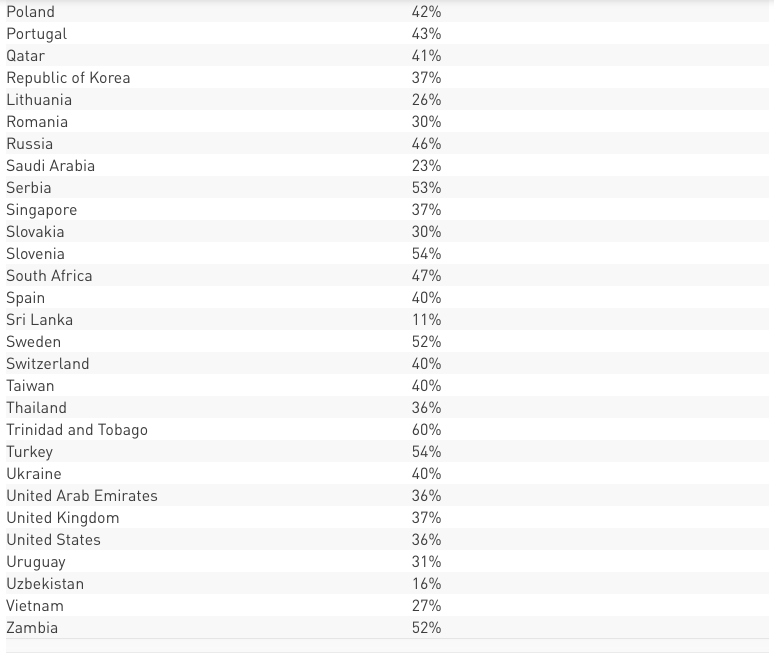
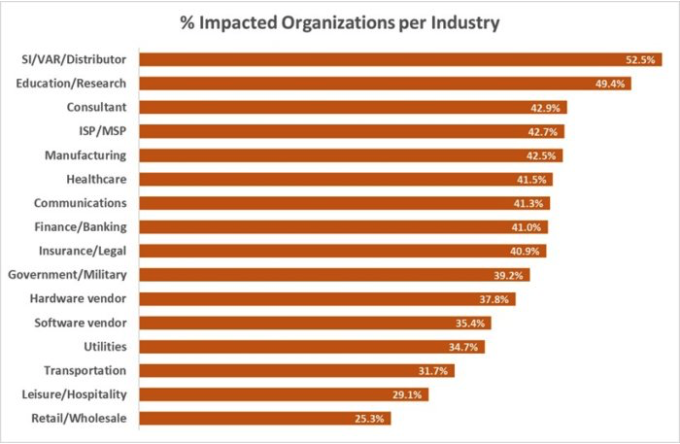
CORPORATE NUMBERS IMPACTED BY COUNTRIES
The spread per countries is overwhelming and crosses continent and regions, ranging to over 90 countries in all regions. The impact itself is also wide and reaches peaks of countries seeing over 60% of corporate networks impacted, and many distributions seeing over 50% of corporate networks within the country beings impacted.
A detailed breakdown per countries included in Annex 1
CONCLUSION
This vulnerability, because of the complexity in patching it and easiness to exploit, seems that it will stay with us for years to come, unless companies and services take immediate action to prevent the attacks on their products by implementing a protection.
Since the outbreak of the COVID-19 pandemic, society has already gotten used to learning about variants, spread and other terminology that is taken from epidemiology theories. The phenomena the world is witnessing with the exploitation of this vulnerability is very much identical.
Given the upcoming holiday seasons, when security teams may be slower to implement protective measure, the threat is imminent. This acts precisely like a cyber pandemic — highly contagious, spreads rapidly and has multiple variants, which force more ways to attack.
Annex 1 – Detailed breakdown – Impact per country