By Denny Wan, peer reviewed by Chip Block and Donna Gallaher
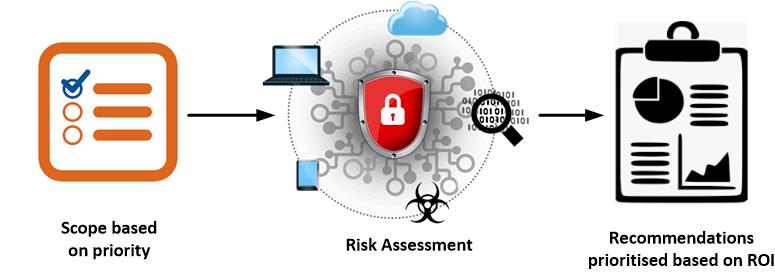
Targeting can be applied to the following tasks in the investment decision process based on the potential financial loss against an asset:
- Prioritising the risk assessment scope
- Prioritising the recommendations on remediation actions
In this article, I reflect on the discussions with Chip and Donna on the business need for targeting cyber security investments. We discussed how to apply the FAIR approach to the cyber security budget prioritisation process leveraging the above targeting effort. We are seasoned cyber security executives and chairs of our local FAIR Institute Chapters, which I will address later. The paper concludes by explaining how to use the security ROI dashboard and scorecard to assist in the investment prioritisation process
IMF forecasted a weakening of the global economy in 2019 which, for most firms, will inevitably result in some level of budget cuts. Unfortunately, cyber security spending is often the target for the cut because it generally does not result in direct revenue impact. However, executives must approach risk prioritisation decisions with caution since cyber breaches can impact customers and other third parties along the supply chain. If the organisation is found to be negligent in their risk management decisions, putting profit before customer security without due considerations, they can be exposed to significant punitive fines and damages which are not covered by cyber insurance. The Open Group FAIR (Factor Analysis of Information Risk) methodology is a structured approach to quantifying potential financial losses attributed to cyber risk. This is a powerful defence for organisations to justify their budget prioritisation decisions.
How much less risk will we have?
This was the infamous question put to Jack Jones (author of the FAIR framework) in 2001 as the CISO of Nationwide Insurance when discussing his (then) information security strategy. The best answer he could offer was to shrug his shoulder and reply “Less”. The executive knew he wasn’t going to get a better answer but wanted to make a point. Sounds familiar? Jack knew the questions deserved an answer that could be defended and was useful to the business. It sowed the seed for the FAIR risk quantification methodology. He made it his mission to decompose risk into something he and an executive could understand.
Fast forward to 2019; the picture isn’t all that dissimilar:
Source: The FAIR Institute
The above picture succinctly and humorously captures the business communication challenge on managing cyber security.
FAIR Risk Quantification Methodology has matured since its initial release in 2009 and remains the only open sourced approach surviving the scrutiny of the Open Group and global risk management professional communities. It is a powerful communication tool for bridging the perceived communication challenge depicted above. Membership in the FAIR Institute, the voice of the FAIR community, has enjoyed year-on-year growth of more than 25%, exceeding 5,600 members worldwide. There are over 400 blog articles published by the FAIR Institute, including many practical tools, tutorials, video guides and interviews. There are several simulation tools such as FAIR-U and statistical packages for R. It is a vibrant and active community.
Cyber breaches can be costly
The 2013 Target data breach which impacted 110 million shoppers was reported to have cost $292 million in primary losses in Target’s 2016 annual report. Additionally, the secondary losses from several class actions totalled $153.9 million. Target’s CEO resigned from the fallout.
It was also a hard lesson for Yahoo where its valuation was reduced by $350 million due to previously undisclosed data breaches in 2013 and 2014. But the carnage did not stop there. Earlier this year, former Yahoo directors settled on a $29 million shareholder derivative lawsuit for their handling of these data breaches. The settlement is a noteworthy departure from other normally unsuccessful breach-related derivative lawsuits because it held the directors directly fiducially responsible. As the number of data breach derivative lawsuits against directors and officers continues to increase, the large settlements may create valuation expectations that increase settlement costs of other pending and future data breach-related derivative cases. The suit alleged that Yahoo officials breached their fiduciary duties by failing to protect Yahoo’s data. They also failed to investigate and remediate the breaches after they occurred by neglecting to put proper safety mechanisms in place to prevent such attacks (i.e., “the Board’s refusal to spend the necessary money to improve [Yahoo’s] data security infrastructure exposed [Yahoo] to significant hacking incidents”). Finally, Yahoo was also accused of issuing false and misleading statements about their knowledge of the data breaches.
In June 2019, rating agency Moody’s Corp and Israeli cyber group Team8 announced a joint venture to assess how vulnerable businesses are to cyber-attacks and create what they hope will become a global benchmark. Similar to the way that banks can check their stability with a stress-test, Moody’s and Team8 are developing a framework to measure companies’ defences and preparedness for such attacks in comparison to other businesses and over time. According to Derek Vadala (chief executive of the joint venture), the service will be a tool for companies engaging in mergers and acquisitions or when purchasing cyber insurance policies. The cyber health of companies can impact credit ratings. In March, Standard & Poor’s downgraded Atlanta-based credit bureau Equifax reflecting the possible fallout from a 2017 data breach. Moody’s in May downgraded its outlook of Equifax citing the breach as the reason for the change. This rating service could be a structured tool for lenders to justify an increase in the interest rate to compensate against the perceived cyber risk as premiums in a loan, directly impacting the cost of capital.
Therefore, it would be useful for business executives to equip themselves with cyber risk modelling knowledge and tools to understand these new cyber risk assessment process. And, unfortunately, cyber risk assessment process and penetration testing results tend not to include any specific dimensioning of the potential financial impacts. On the other hand, it is unlikely that cyber risk rating agencies such as the new Moody’s-Team8 joint venture will be undertaking, or allowed to undertake, cyber risk assessment or penetration testing on the companies they are assessing. They will apply their proprietary cyber risk quantification methodology and tools for these assessments. Therefore, it could be very difficult for the target companies to challenge or refute an unfavourable assessment without building their cyber risk quantification models.
The Slack Pre-emptive strike
But not every company takes the cyber risk challenge lying down. Chip explained in his recent article titled “The Slack IPO – The Role of Risk Quantification in Investing and the Lack of Faith in Insurance” that Slack took the unusual approach by drawing attention to two cyber risks:
- It cannot assure that it can sufficiently mitigate the risk from cyber attacks
- It cannot be certain that its cyber liability insurance cover will be available or adequate for all liabilities
Slack’s share price surged 50% to $38.5 (over the reference price of $26) when it was opened to trading. The current share price is still hovering at around $36. Such disclosure did not dampen enthusiasm for the stock. But to put the situation into perspective, Slack lost $138 million last year on revenue of $400 million. So perhaps the risk appetite of the investors differs to that of lenders assessing the capital raising request of a more mature business such as Yahoo or Target US. For these companies, an unfavourable cyber risk assessment might have a material impact on their borrowing costs. Their cyber security investment decisions or cuts to their cyber risk program budgets will attract much more scrutiny.
Return on Security Investment (ROSI)
Moreover, it is an established business practice to prioritise investment decisions based on Return on Investment (ROI) calculations. However, the prioritisation of investment in cyber security controls requires extending the concept of ROI to ROSI (Return on Security Investment) as depicted in the formula below:
Cyber security primarily focusses on minimising financial losses to the organisation and its clients or partners. The ROSI is usually much higher than 100%, often in the ranges of 1000%-2000%. This might feel counter-intuitive because ROI is traditionally in the 10%-20% range. This is where the skill of an experienced vCISO is needed to interpret ROSI. To illustrate a typical ROI, consider car insurance. The ‘Monetary loss reduction’ (in the event of an accident) is the insured amount for the vehicle where the ‘Cost of the solution’ is the premium. The ratio of insured amounts to premiums should be in the order of 1:10 to 1:50, giving rise to a ROSI of 1000% – 5000%.
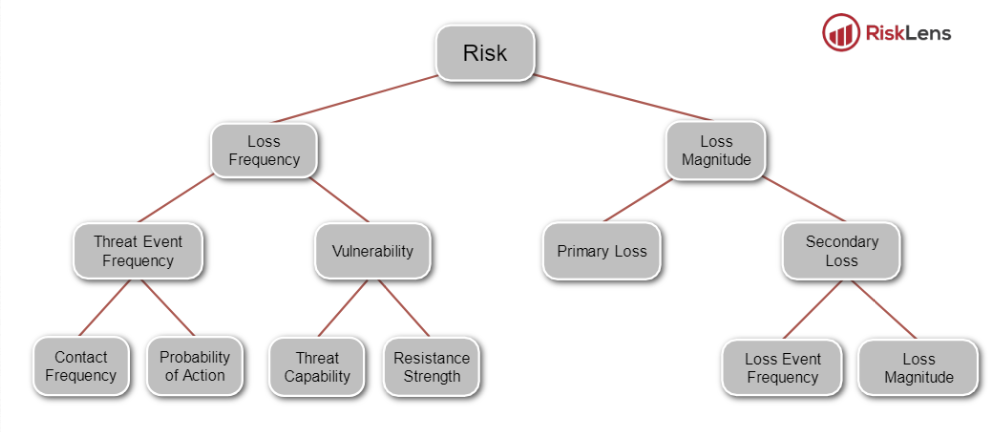
Moreover, estimating financial losses attributed to cyber-attacks is not straight forward because it requires specialised skills to estimate the probable frequency of successful attacks. Although we can calculate the cost of a given data breach after it has occurred, it is more difficult to predict the frequency and likelihood of attacks succeeding in a financial period. The FAIR framework breaks down the estimation of threat frequent into ‘Contact Frequency’ and ‘Probability of Action’, making it possible to perform such estimations. The taxonomy of the FAIR framework is depicted below, showing the break down of the core components:
Source: The FAIR Risk Taxonomy Standard (O-RT)
The cyber security ROI Dashboard and security scorecard for investment effectiveness
The cyber security ROI dashboard and the scorecard are practical tools to support the investment prioritisation process. It is designed to answer the following question:
How much less risk we will have?
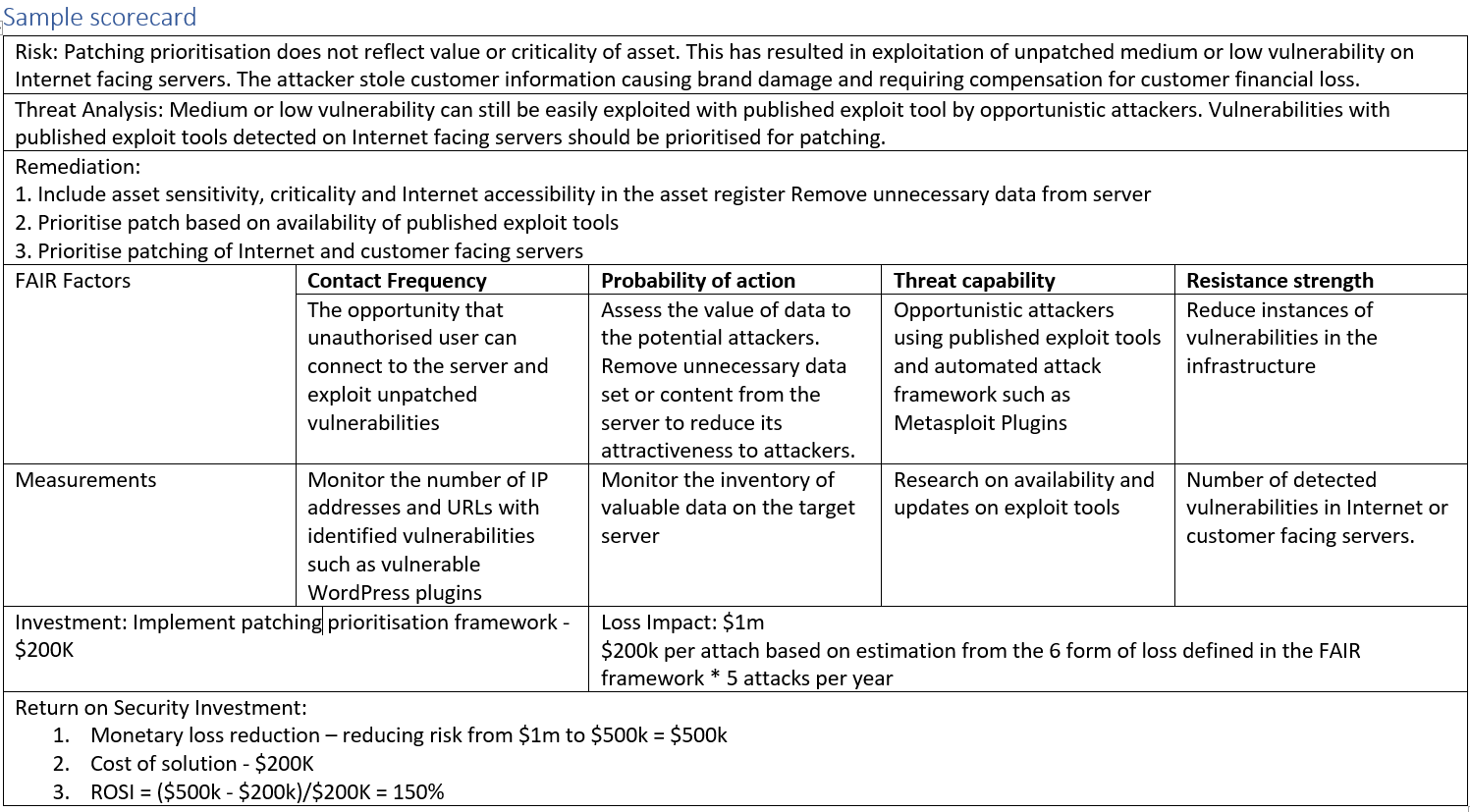
Below is a sample scorecard for investment effectiveness. The scorecard is not a risk assessment process. The inputs to the scorecard are:
- Risks identified from the risk assessment process
- The threat analysis underpinning the risk identification process
- The recommended remediation options
The scoring process accepts the result of the risk assessment process on its face value. The process assesses:
- Whether the mitigation option address the identified risk using the FAIR factors analysis?
- What measurements can be used to monitor the effectiveness of the remediation process?
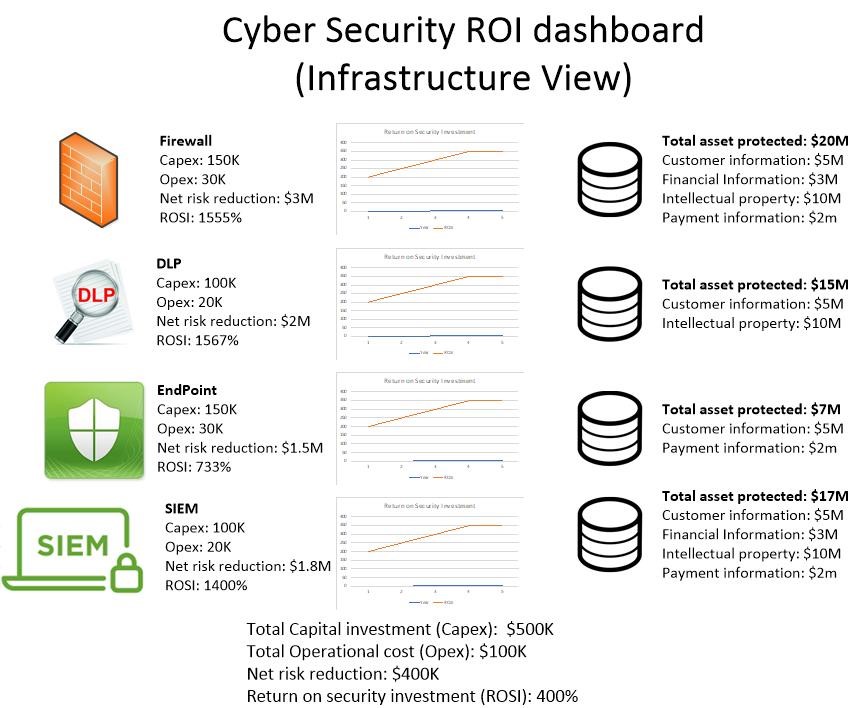
This scoring process can be applied against different remediation solutions such as firewall, DLP (Data Lead Protection) etc. The analysis can be drilled downed further into each of these solution classes. For example, a firewall refresh program can be staggered based on scoring to ease the business impact and CapEx requirements. The scoring result is depicted in the following high-level dashboard:
Conclusion
Prioritisation of cyber security investment is a step in the IT risk governance maturity process. The FAIR methodology focusing on minimising financial loss aligns with accepted business investment prioritisation practice. The increasing awareness of the impact of cyber risk on business can impact the cost of capital. A major step in helping organizations is making quantified risk operational and part of the day to day decisions of businesses. The scorecard for cyber security investment effectiveness and ROI dashboard are useful visual tool to assist in the investment prioritisation decision process and supporting the operational application of quantified risks for organizations.
About the author:
 Denny Wan is a cyber security expert with over 20 years experience in the Australian IT security sector. He is the principal consultant of Security Express and the chair of the Sydney Chapter of the FAIR Institute with deep expertise in Cyber Risk Economics. It is an effective approach for prioritising cyber security investments and to explain its business values. He is a certified PCI QSA and CISSP. He is a postgraduate researcher at the Optus Macquarie University Cyber Security Hub researching into cyber risk management in the supply chains. This is a useful model for managing 3rd party supplier risks under compliance framework such as APRA CPS 234.
Denny Wan is a cyber security expert with over 20 years experience in the Australian IT security sector. He is the principal consultant of Security Express and the chair of the Sydney Chapter of the FAIR Institute with deep expertise in Cyber Risk Economics. It is an effective approach for prioritising cyber security investments and to explain its business values. He is a certified PCI QSA and CISSP. He is a postgraduate researcher at the Optus Macquarie University Cyber Security Hub researching into cyber risk management in the supply chains. This is a useful model for managing 3rd party supplier risks under compliance framework such as APRA CPS 234.
About the reviewers:
Chip Block is the Vice President and Chief Solutions Architect at Converged Security Solutions and chair of the Great Washington DC Area Chapter of the FAIR Institute. He has been working in the high technology arena for over 30 years and enjoys the challenge of taking organizations working at the leading edge and growing them into vibrant and successful companies. Over his career, he has been fortunate to have worked on all sides of the business equation, from startup companies, to IPO companies, to Government contracting to international sales. He is the recipient of an R&D 100 award for the development of one of the top one hundred new product technologies in the world. His ongoing work with state of the art technology and operations include research into critical areas such as cyber protection of medical devices, the impact of the insurance industry on the cyber market and transitional cloud strategies.
Donna Gallaher is the President and CEO of New Oceans Enterprises, LLC, an Information Security and Operational Risk Management Advisory Services firm providing fractional/virtual external CISO and data privacy services to CEOs and Boards of Directors. She serves on the Board of Advisors for the FAIR Institute and as the chair the Atlanta FAIR Institute Chapter. She is a thought leader in security executive leadership and a champion of the vCISO movement. Donna is a regular contributor to the National Technology Security Coalition which serves as the “voice of the CISO” in the United States by uniting public and private sector stakeholders around policies that improve national cybersecurity standards and awareness.