Hackers are designing sophisticated phishing attacks impersonating household names in order to bypass security filters to gain foothold into corporate networks.
- Hackers hijack Oxford’s email server to send malicious emails to victims
- 43% of these attacks targeted European companies, while the rest were seen in Asia and Middle East
- Hackers utilise a Samsung domain hosted on an Adobe server that was left unused since 2018’s Cyber Monday event
Hackers hijacked Oxford University’s email server to send malicious emails to victims. The emails contained links that redirected to an Adobe server used by Samsung in the past, enabling hackers to leverage the façade of a legitimate Samsung domain to successfully trick victims. Ultimately, victims were led down a deceitful path to share their Office 365 log-in credentials.
Oxford’s Email Server Hijacked
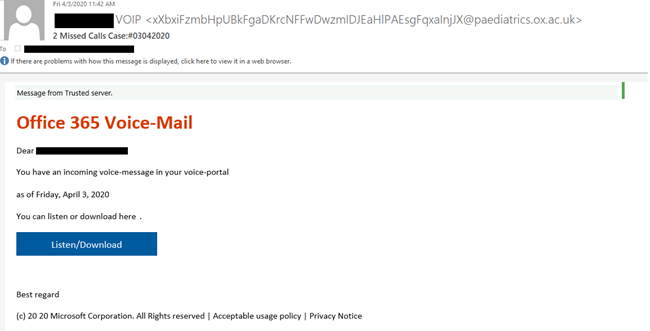
In early April 2020, Check Point researchers began observing emails sent to victims titled “Office 365 Voice Mail”. The emails alleged that an incoming voice-message was waiting in a victim’s voice-portal, prompting users to click on a button that would allegedly take them to their Office 365 account to take further action. After the victims clicked the button, they were redirected to a phishing page masquerading as the Office 365 login page. Below is an example email:
Most of the emails came from multiple generated addresses belonging to legitimate subdomains from different departments at the University of Oxford. The email headers show that the hackers found a way to abuse one of Oxford’s SMTP (simple mail transfer protocol) servers, an application that’s primary purpose is to send, receive, and/or relay outgoing mail between email senders and receivers. The use of legitimate Oxford SMTP servers enabled hackers to pass the reputation check required by security measures for the sender domain.
Redirections from Samsung’s Trusted URL
Over the past year, Google and Adobe open redirects have been used by phishing campaigns in order to add legitimacy to the URLs used in the spam emails. An open redirect is an URL on a web site that can be used by anyone to redirect users to another site. In this case, the links in the email redirected to an Adobe server previously used by Samsung during a 2018 Cyber Monday marketing campaign. In other words, the link embedded in the original phishing email is part of the trusted Samsung domain stem – one that unknowingly redirects victims to a website hosted by the hackers. By using the specific Adobe Campaign link format and the legitimate domain, the attackers increased the chances for the email to bypass email security solutions based on reputation, blacklists and URL patterns.
Safety Tips for Office 365 Users
- Use different passwords for your cloud application. Segregation protects your assets when one is exposed.
- Use cloud and mail security solutions. The fact these campaigns thrive proves native security solution are easy to bypass – use cloud and mail security solutions to remove threats getting into your email and protecting you cloud infrastructure.
- Don’t enter your credentials when you didn’t expect to do it. Often, it’s a scam in disguise.
Check Point has informed Oxford University, Adobe and Samsung of its findings. Adobe took the relevant actions to prevent this type of attack through its server across all customers.