Following Microsoft’s news about Hafnium, the Australian Cyber Security Centre (ACSC) advises organisations using Microsoft Exchange to urgently patch the following Common Vulnerabilities and Exposures (CVEs):
- CVE-2021-26855 – server-side request forgery (SSRF) vulnerability in Exchange.
- CVE-2021-26857 – insecure deserialization vulnerability in the Unified Messaging service.
- CVE-2021-26858 – post-authentication arbitrary file write vulnerability in Exchange.
- CVE-2021-27065 – post-authentication arbitrary file write vulnerability in Exchange.
If successfully exploited, these CVEs would allow an unauthenticated attacker to write files and execute code with elevated privileges on the underlying Microsoft Windows operating system.
A large number of Australian organisations are yet to patch vulnerable versions of Microsoft Exchange, leaving them vulnerable to compromise. The ACSC is encouraging these organisations to do so urgently.
Assistant Minister for Defence, the Hon Andrew Hastie MP, said Australian organisations should take immediate steps to urgently patch vulnerable systems.
“Australian organisations cannot be complacent when it comes to cyber security, which is why all users of Microsoft Exchange are being urged to patch their vulnerable systems,” Assistant Minister Hastie said.
“The ACSC has identified a large number of Australian organisations yet to patch affected versions of Microsoft Exchange, leaving them exposed to cyber compromise.
“This can be done by implementing the necessary network security patches as soon as possible and then following the detection steps outlined by Microsoft.
“If organisations are unable to quickly deploy these patches, they should consider preventing internet access to the exchange web server.”
The ACSC recommends that organisations implement web shell mitigation steps and continues to monitor and investigate the situation. The ACSC is able to provide assistance as required.
HAFNIUM: Advice about the new nation-state attack from Sophos on Vimeo.
Mat Gangwer, Senior Director, Sophos Managed Threat Response stated “These vulnerabilities are significant and need to be taken seriously. They allow attackers to remotely execute commands on these servers without the need for credentials, and any threat actor could potentially abuse them. The broad installation of Exchange and its exposure to the internet mean that many organisations running an on-premises Exchange server could be at risk.
Attackers are actively exploiting these vulnerabilities with the primary technique being the deployment of web shells. This, if unaddressed could allow the threat actor to remotely execute commands for as long as the web shell is present.
Organisations running an on-premises Exchange server should assume they are impacted, and first and foremost patch their Exchange devices and confirm the updates have been successful. However, simply applying patches won’t remove artifacts from your network that pre-date the patch. Organisations need human eyes and intelligence to determine whether they have been impacted and to what extent, and, most importantly to neutralise the attack and remove the adversary from their networks.
Organisations should review the server logs for signs that an attacker may have exploited their Exchange server. Many of the current known indicators of compromise are web shell-based, so there will be file remnants left in the Exchange server. An overview of files and any modifications to them is therefore important. If you have an endpoint detection and response (EDR) product installed, you can also review logs and process command execution.
If you find any anomalous or suspicious activity, you should determine your exposure as this will allow you to decide what to do next. You need to understand how long or impactful this activity may have been. What is the gap between appearance of the web shell or other artifacts in your network and the moment of patching or discovery? This is often a good time to ask for external support if you’re not sure what to do. Third-party forensic and incident response can be vital at this stage, providing experienced threat hunting and human intelligence that can dive deep into your network and find the attackers.
Kaspersky’s Advisory:
Kaspersky products detect and protect against exploitation attempts of the recently discovered Microsoft Exchange Server vulnerabilities using Behavior Detection and Exploit Prevention components. The detection name is PDM:Exploit.Win32.Generic. Kaspersky also detects the relevant exploits, as well as the payloads being used after the exploitation with the several detection names, including but not limited to:
∙ Exploit.Win32.CVE-2021-26857.gen
∙ HEUR:Exploit.Win32.CVE-2021-26857.a
∙ HEUR:Trojan.ASP.Webshell.gen
∙ HEUR:Backdoor.ASP.WebShell.gen
∙ UDS:DangerousObject.Multi.Generic
Have a read on how our products protect from these threats is here: https://securelist.com/zero-day-vulnerabilities-in-microsoft-exchange-server/101096/
Kaspersky experts anticipate a growing number of exploitation attempts with the purpose of gaining access to resources inside corporate perimeters accompanied by a high risk of ransomware infection and data theft. Therefore, Kaspersky strongly recommends that businesses update Exchange Server as soon as possible. More information about how Kaspersky protects its users from this threat is available here.
Number of APT groups exploiting the latest Exchange vulnerabilities grows, with thousands of email servers under siege, ESET discovers
Updated 11 March – ESET Research has discovered that more than ten different advanced persistent threat (APT) groups are exploiting the recent Microsoft Exchange vulnerabilities to compromise email servers. ESET has identified more than 5,000 email servers that have been affected by malicious activity related to the incident. The servers belong to organizations – businesses and governments alike – from around the world, including high-profile ones. Thus, the threat is not limited to the widely reported Hafnium group.
In early March, Microsoft released patches for Exchange Server 2013, 2016 and 2019 that fix a series of pre-authentication remote code execution (RCE) vulnerabilities. The vulnerabilities allow an attacker to take over any reachable Exchange server, without the need to know any valid account credentials, making internet-connected Exchange servers especially vulnerable.
“The day after the release of the patches, we started to observe many more threat actors scanning and compromising Exchange servers en masse. Interestingly, all of them are APT groups focused on espionage, except one outlier that seems related to a known coin-mining campaign. However, it is inevitable that more and more threat actors, including ransomware operators, will have access to the exploits sooner or later,” says Matthieu Faou, who is leading ESET’s research effort into the recent Exchange vulnerability chain. ESET researchers noticed that some APT groups were exploiting the vulnerabilities even before the patches were released. “This means we can discard the possibility that those groups built an exploit by reverse engineering Microsoft updates,” adds Faou.
ESET telemetry flagged the presence of webshells (malicious programs or scripts that allow remote control of a server via a web browser) on more than 5,000 unique servers in over 115 countries.
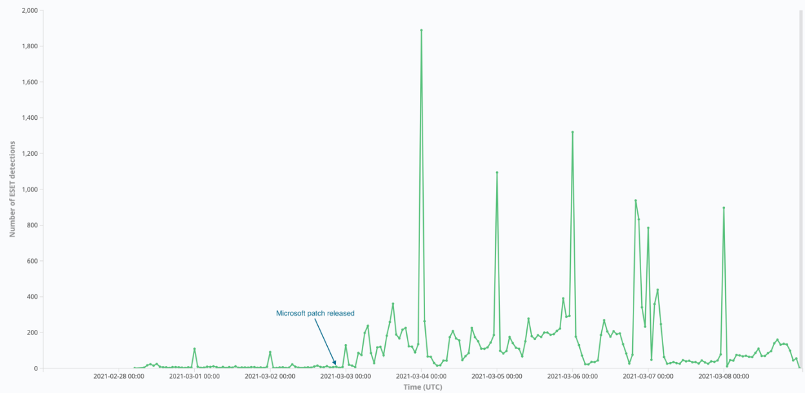
ESET hourly detections for webshells dropped via CVE-2021-26855 – one of the recent Exchange vulnerabilities
Proportion of webshell detections by country (2021-02-28 to 2021-03-09)
ESET has identified more than ten different threat actors that likely leveraged the recent Microsoft Exchange RCE vulnerabilities in order to install malware like webshells and backdoors on victims’ email servers. In some cases, several threat actors were targeting the same organization.
The identified threat groups and behavior clusters are:
- Tick – compromised the web server of a company based in East Asia that provides IT services. As in the case of LuckyMouse and Calypso, the group likely had access to an exploit prior to the release of the patches.
- LuckyMouse – compromised the email server of a governmental entity in the Middle East. This APT group likely had an exploit at least one day before the patches were released, when it was still a zero day.
- Calypso – compromised the email servers of governmental entities in the Middle East and in South America. The group likely had access to the exploit as a zero day. In the following days, Calypso operators targeted additional servers of governmental entities and private companies in Africa, Asia and Europe.
- Websiic – targeted seven email servers belonging to private companies (in the domains of IT, telecommunications and engineering) in Asia and a governmental body in Eastern Europe. ESET named this new cluster of activity as Websiic.
- Winnti Group – compromised the email servers of an oil company and a construction equipment company in Asia. The group likely had access to an exploit prior to the release of the patches.
- Tonto Team – compromised the email servers of a procurement company and of a consulting company specialized in software development and cybersecurity, both based in Eastern Europe.
- ShadowPad activity – compromised the email servers of a software development company based in Asia and a real estate company based in the Middle East. ESET detected a variant of the ShadowPad backdoor dropped by an unknown group.
- The “Opera” Cobalt Strike – targeted around 650 servers, mostly in the US, Germany, the UK and other European countries just a few hours after the patches were released.
- IIS backdoors – ESET observed IIS backdoors installed via webshells used in these compromises on four email servers located in Asia and South America. One of the backdoors is publicly known as Owlproxy.
- Mikroceen – compromised the exchange server of a utility company in Central Asia, which is the region this group typically targets.
“It is now clearly beyond prime time to patch all Exchange servers as soon as possible. Even those not directly exposed to the internet should be patched. In case of compromise, admins should remove the webshells, change credentials and investigate for any additional malicious activity. The incident is a very good reminder that complex applications such as Microsoft Exchange or SharePoint should not be open to the internet,” advises Faou.