The APT group uses innovative methods to further spread their malicious payloads
 ESET researchers have discovered new tools used by the Gamaredon group in their latest malicious campaigns. The first tool targets Microsoft Outlook using a custom Microsoft Outlook Visual Basic for Applications (VBA) project and allows the attackers to use the victim’s email account to send spearphishing emails to contacts in the address book. Using Outlook macros to deliver malware is something rarely seen by researchers. The second tool is used by the notoriously active APT group to inject macros and references to remote templates into Office documents – Word and Excel. Both are designed to help the Gamaredon group spread further in already compromised networks.
ESET researchers have discovered new tools used by the Gamaredon group in their latest malicious campaigns. The first tool targets Microsoft Outlook using a custom Microsoft Outlook Visual Basic for Applications (VBA) project and allows the attackers to use the victim’s email account to send spearphishing emails to contacts in the address book. Using Outlook macros to deliver malware is something rarely seen by researchers. The second tool is used by the notoriously active APT group to inject macros and references to remote templates into Office documents – Word and Excel. Both are designed to help the Gamaredon group spread further in already compromised networks.
“In the last few months, there has been an increase in activity from this group, with constant waves of malicious emails hitting their targets’ mailboxes. The attachments to these emails are documents with malicious macros that, when executed, try to download a multitude of different types of malware,” says Jean-Ian Boutin, Head of Threat Research at ESET.
The latest tools inject malicious macros or references to remote templates into existing documents on the attacked system, which is a very efficient way of moving within an organization’s network, as documents are routinely shared amongst colleagues. Furthermore, thanks to a special functionality that tampers with the Microsoft Office macro security settings, the affected users have no idea that they are again compromising their workstations whenever they open the documents.
The group uses backdoors and file stealers to identify and collect sensitive documents on a compromised system to be uploaded to the C&C server. Furthermore, these file stealers have the capability to execute arbitrary code from the C&C server.
There is one major distinction between Gamaredon and other APT groups – the attackers make little to no effort to stay under the radar. Even though their tools have the capacity to use stealthier techniques, it seems this group’s main focus is to spread as far and fast as possible in their target’s network while trying to exfiltrate data.
“While abusing a compromised mailbox to send malicious emails without the victim’s consent is not a new technique, we believe this is the first publicly documented case of an attack group using an OTM file and Outlook macro to achieve it,” explains Boutin about the ESET discovery. “We were able to collect numerous different samples of malicious scripts, executables and documents used by the Gamaredon group throughout their campaigns.”
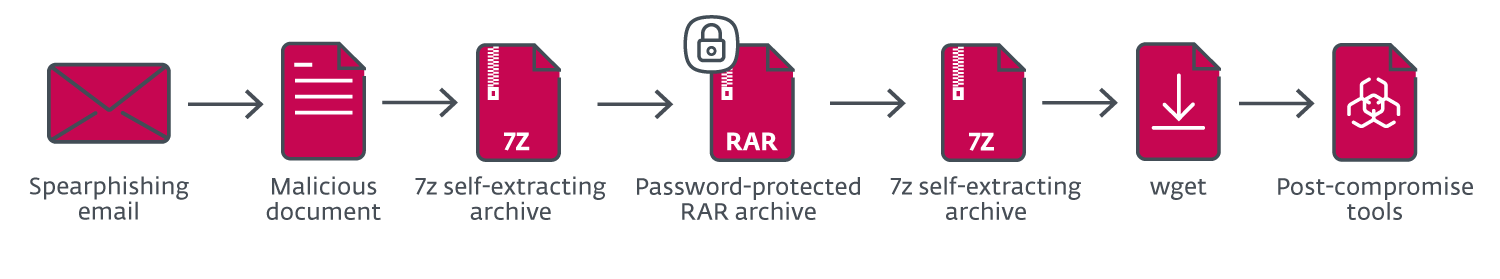
“Typical compromise chain in a Gamaredon campaign”
Gamaredon group has been active since at least 2013. It has been responsible for a number of attacks, mostly against Ukrainian institutions.
Tools discussed in this research are detected as variants of MSIL/Pterodo, Win32/Pterodo or Win64/Pterodo by ESET’s products.
For more technical details about Gamaredon’s latest tools, read the full blog post “Gamaredon group grows its game” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.





