
By Martin Rakhmanov, Security Research Manager, SpiderLabs at Trustwave
In this blog, I will be discussing three security issues found in several SolarWinds products. All three are severe bugs with the most critical one allowing remote code execution with high privileges. To the best of Trustwave’s knowledge, none of the vulnerabilities were exploited during the recent SolarWinds attacks or in any “in the wild” attacks. However, given the criticality of these issues, we recommend that affected users patch as soon as possible. We have purposely left out specific Proof of Concept (PoC) code in this post in order to give SolarWinds users a longer margin to patch but we will post an update to this blog that includes the PoC code on Feb. 9.
SolarWinds Orion Platform Vulnerability (CVE-2021-25275): Database Credentials for Everyone
In light of the recent SolarWinds supply chain attack, I decided to take a quick look at SolarWinds products based on the Orion framework. SolarWinds offers trial versions for download. I picked User Device Tracker and installed it on a vanilla Windows Server 2019 virtual machine. As a part of the installation, there is a setup of Microsoft Message Queue (MSMQ), which has been around for more than two decades. This immediately grabbed my attention since, by default, this technology is not installed on modern Windows systems. Next, the installer suggested installing Microsoft SQL Server Express for the product backend database management, but I could have opted to use an existing Microsoft SQL Server instance too. After a few more steps – voilà – we have the product up and running.
My first step was to check how well SolarWinds secured the credentials for the backend database since database security is a research area we care about very much. After simple grep across the files installed by the product, one file was found (well, actually two, but more on that later), as shown in Figure 1.
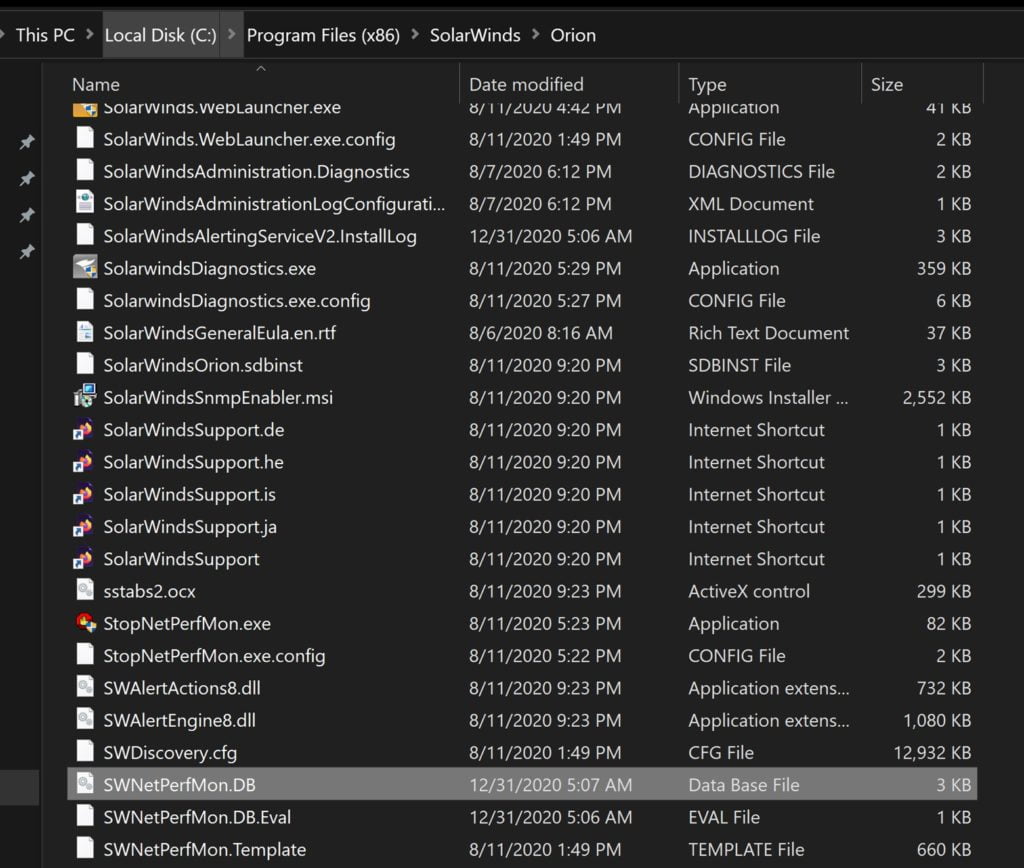
Permissions are generously granted to all locally authenticated users, as shown in Figure 2.
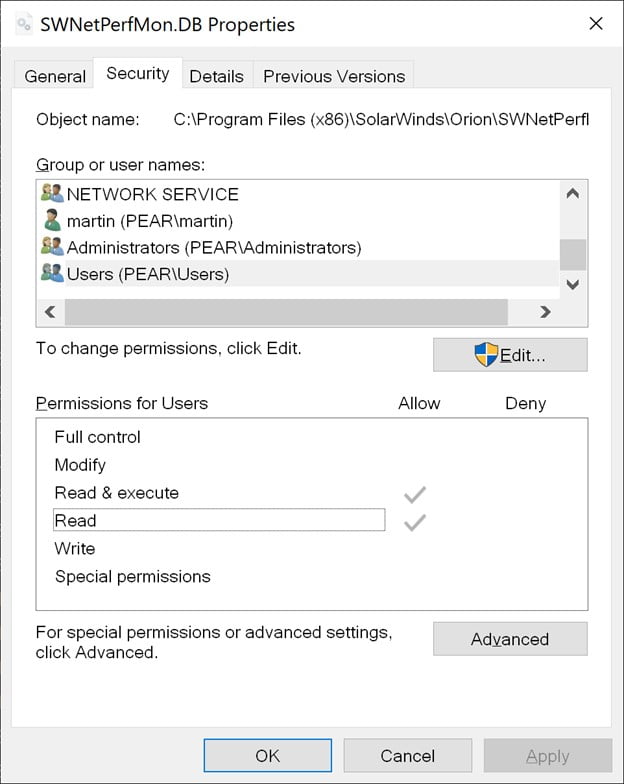
Inside this file, we find credentials for the SolarWinds backend database called SOLARWINDS_ORION:

I spent some time finding code that decrypts the password but essentially, it’s a one-liner. In the end, unprivileged users who can log in to the box locally or via RDP will be able to run decrypting code and get a cleartext password for the SolarWindsOrionDatabaseUser. We are withholding all Proof of Concept (PoC) code for these vulnerabilities to give users a little more time to patch, but you’ll be able to test this out for yourselves next week on Feb. 9. The next step is to connect to the Microsoft SQL Server using the recovered account, and at this point, we have complete control over the SOLARWINDS_ORION database. From here, one can steal information or add a new admin-level user to be used inside SolarWinds Orion products.
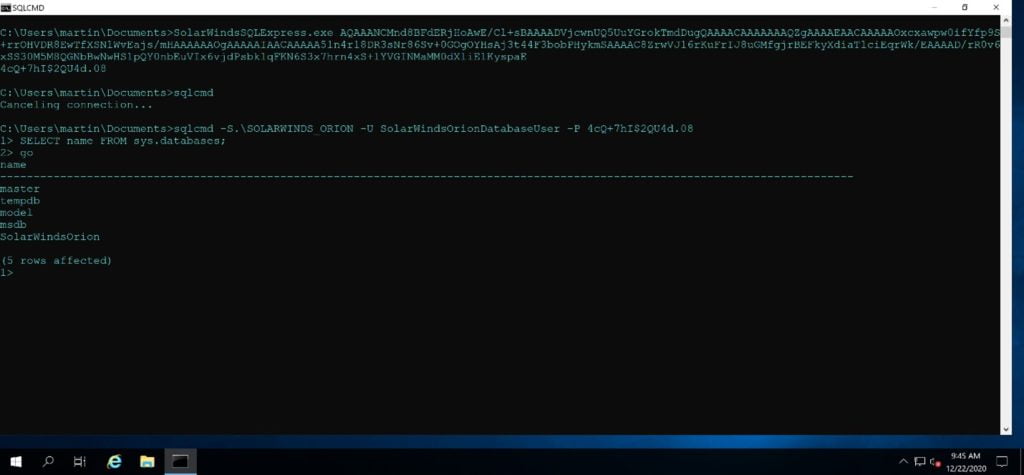
As mentioned earlier, I performed my tests on the trial version and when verifying the patch noticed that while it secures the SWNetPerfMon.DB file it does not secure the SWNetPerfMon.DB.Eval found in the trial.
This concludes the section about configuration file insecure storage. On to the next finding!
SolarWinds Orion Platform Vulnerability (CVE-2021-25274): Messages Queued, Processed, Deserialized and Exploited
Alright, the previous vulnerability requires local access to the server – even if that access is unprivileged. What about getting complete control over SolarWinds remotely without having any credentials? I mentioned MSMQ technology earlier, so the next thing I tried was to open the Computer Management console and see what’s going on under the Message Queuing, as you can see in Figure 5.
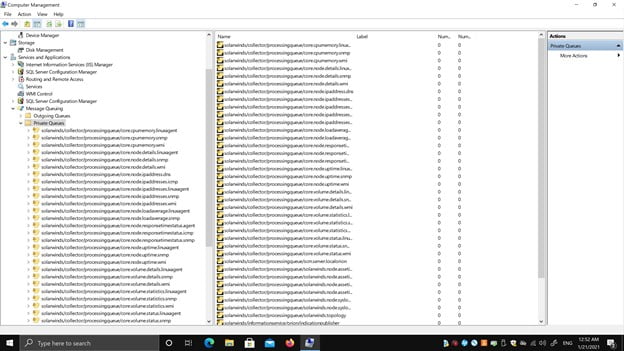
As you can see, there is a huge list of private queues, and literally every one of them has a specific problem. See if you can pinpoint it in Figure 6 below.
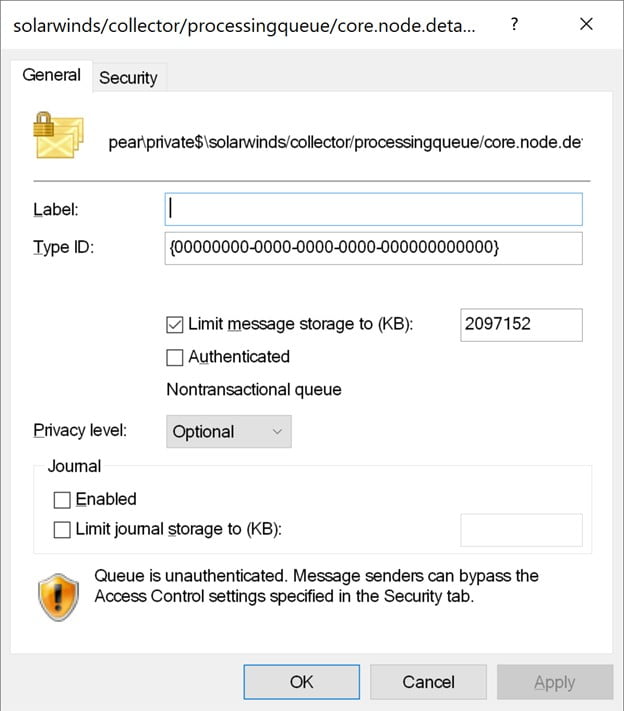
It’s pretty hard to miss that warning shield showing that the queue, like all the queues, is unauthenticated. In short, unauthenticated users can send messages to such queues over TCP port 1801. My interest was piqued and I jumped in to look at the code that handles incoming messages. Unfortunately, it turned out to be an unsafe deserialization victim. A simple Proof of Concept (PoC) (which again, we will be releasing Feb. 9) allows remote code execution by remote, unprivileged users through combining those two issues. Given that the message processing code runs as a Windows service configured to use LocalSystem account, we have complete control of the underlying operating system.
After the patch is applied, there is a digital signature validation step performed on arrived messages so that messages having no signature or not signed with a per-installation certificate are not further processed. On the other hand, the MSMQ is still unauthenticated and allows anyone to send messages to it.
SolarWinds Serv-U FTP Vulnerability (CVE-2021-25276) — FTP Server: Let Me Add an Admin User for Myself
Finally, I took a quick look at another SolarWinds product called Serv-U FTP for Windows. It turns out that the accounts are stored on disk in separate files. Directory access control lists allow complete compromise by any authenticated Windows user. Specifically, anyone who can log in locally or via Remote Desktop can just drop a file that defines a new user, and the Serv-U FTP will automatically pick it up. Next, since we can create any Serv-U FTP user, it makes sense to define an admin account by setting a simple field in the file and then set the home directory to the root of C:\ drive. Now we can log in via FTP and read or replace any file on the C:\ since the FTP server runs as LocalSystem.
Summary
In this post, we discussed two findings in SolarWinds Orion User Device Tracker and one in SolarWinds Serv-U FTP. These issues could allow an attacker full remote code execution, access to credentials for recovery, and the ability to read, write to or delete any file on the system.
Trustwave reported all three findings to SolarWinds, and patches were released in a very timely manner. We want to thank SolarWinds for their partnership during the disclosure process. We recommend that administrators upgrade as soon as possible. We will also be releasing an update to this blog post with Proof of Concept (PoC) code next week on Feb. 9, to give users some additional time to patch. Having direct PoC code helps information security professionals better understand these issues as well as develop protections to prevent exploitation.
Disclosure Timeline
12/30/2020 – Orion vulnerabilities disclosed to vendor
01/04/2021 – Confirmation of Orion CVEs
01/04/2021 – ServU-FTP vulnerabilities disclosed to vendor
01/05/2021 – Confirmation of ServU-FTP CVE
01/22/2021 – Serv-U-FTP hotfix released
01/25/2021 – Orion patches released
02/03/2021 – Advisory published
References
- Fixes are available in the following versions of SolarWinds products:
- Trustwave Advisory TWSL2021-001: https://www.trustwave.com/en-us/resources/security-resources/security-advisories/?fid=28389
Trustwave Protections
Trustwave vulnerability scanning products can detect these vulnerabilities and Trustwave IDS/IPS products include signatures that can detect network exploitation of CVE-2021-25274.
Click here to download the Fact Sheet.





