Check Point Research (CPR) has identified three hacktivist groups peddling false or misleading information in the ongoing Russia-Ukraine conflict.
The groups, named AgainstTheWest, KelvinSecurity and Killnet, are using a combination of old and inaccurate material to publicize themselves, as opposed to assisting the countries involved in the conflict.
CPR has published three case studies that examine the respective groups, where one is either pro-Ukraine or pro-Russia. The case studies point out specific incidences where the groups spread fake information.
Case Study #1: AgainstTheWest
Key Details
- Pro-Ukraine
- Active since October 2021
- Announced collaboration with Anonymous, against Russia
- Claimed to breach Yandex, Russia’s leading search engine
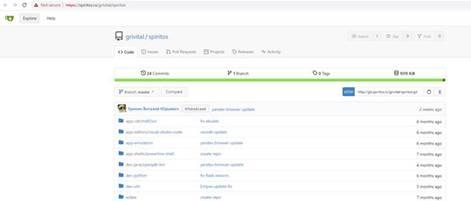
- CPR identified that screenshots and the files posted by the group is a copy of public repository that contains Yandex browser update
Figure 1. “Proof” by AgainstTheWest of Yandex development portal breach
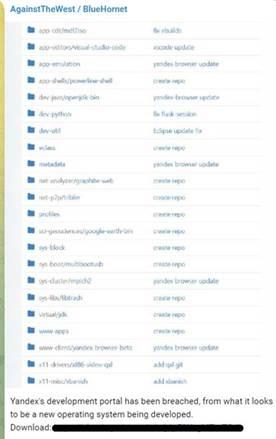
Figure 2. Figure 5: Public repository that contains the same files AgainstTheWest published
Case Study #2: KelvinSecurity
Key Details:
- Defines itself as Private Information Hacker Company
- Pro-Ukraine
- Made the impression that they breached Nuclear Reactor in Joint Institute for Nuclear Research in Russia
- Published a link to the “monitoring system of Nuclear Reactor in Dubna”
- Published a “leaked database from the Russian nuclear institute”
- Published a “video from nuclear reactor”
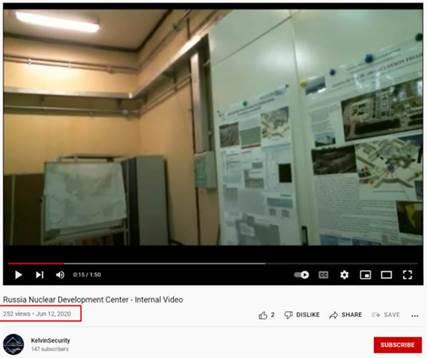
In an effort to verify KelvinSecurity’s claims, CPR found the published database contains a list of presentations by physicists from different institutes and universities across Russia, with some of their personal information, but no sensitive information apart of it. And, that the information about the monitoring system has been openly available years before the conflict, and the “Internal Nuclear Reactor Video” was already published on the YouTube channel of KelvinSecurity group a year ago.
Figure 3. KelvinSecurity publication about nuclear reactor
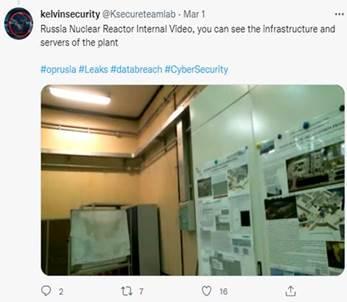
Figure 4. Video on KelvinSecurity Youtube channel from an year ago
Case Study #3: Killnet
Key Details:
- Pro-Russian group
- Recently launched a “KillNet Botnet DDoS” service
- Released a video claiming to have taken down the Anonymous website
As there is no real official Anonymous website, this attack against a generic Anonymous website appears to be more of a morale booster for the pro-Russian side, and a publicity event for KillNet, gathering followers and fans over news and social media than a real attack.
Figure 5. Claim that the website of Anonymous is down
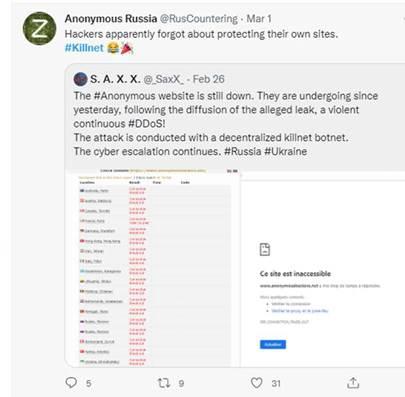
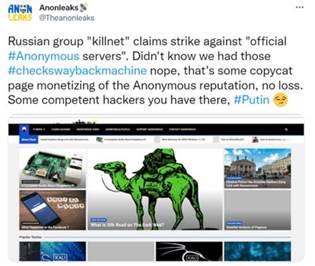
Figure 6. Copycat page called out
“For the first time in history anyone can join a war. We’re seeing the entire cyber community involved, where many groups and individuals have taken a side, either Russia or Ukraine. It’s a lot of cyber chaos. We’re seeing a flood of information from hacktivists making all sorts of claims. Many of these claims are fake. Some of these claims are using old or public information. Hacktivists are designing claims of cyber-attacks to gain popularity or glory. Going forward, it will be important for us all to verify the claims hacktivists and individuals are making in the cyber sphere around the current Ukraine-Russia conflict.” said Lotem Finkelstein, Head of Threat Intelligence and Research at Check Point Software.
“In normal days, when such groups take responsibility for attacks that never happened, it can be dismissed and usually can be ignored. But in days of war, claiming to take control over a nuclear plant, for example, might be a terrible impact on how the two sides respond upon these false claims. As the tension increases, there is little room to validate the reports of cyber-attacks. These hacktivist groups are creating a form of battlefield fog, if you will. It’s important to understand that these hacktivist groups exist regardless of the war, but that they are attempting to take advantage of the moment by spreading misinformation on attacks that never happened for their own clout.” Finkelstein said.
Cyber Safety Guidance
- Beware of fake news. Avoid and be cautious of fast-spreading misinformation.
- Check timestamps. Look out for timestamps on content – you can find yourself sharing old, non-relevant news.
- Trace the origins of content. Be aware of the content you engage with. Where did it originate from? Are you being called to amplify it? Do you have a strong emotional reaction to it? Are you being asked to spend money?
- Double-check the link you get. Always look out for and check links you receive. Are they borrowed from somewhere else? Is it leading to a copied page?
- Rely on sources you trust. Always use information from trustworthy and official sources.