In most cases, fake Flash updates pushing malware are not very stealthy. In recent years, such imposters have often been poorly-disguised malware executables or script-based downloaders designed to install cryptocurrency miners, information stealers, or ransomware. f a victim runs such poorly-disguised malware on a vulnerable Windows host, no visible activity happens, unless the fake updater is pushing ransomware.
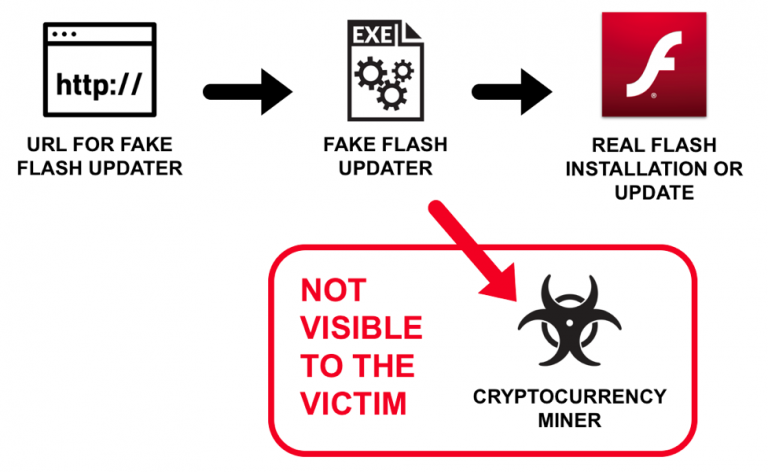
However, a recent type of fake Flash update has implemented additional deception. As early as August 2018, some samples impersonating Flash updates have borrowed pop-up notifications from the official Adobe installer. These fake Flash updates install unwanted programs like an XMRig cryptocurrency miner, but this malware can also update a victim’s Flash Player to the latest version.
Because of the legitimate Flash update, a potential victim may not notice anything out of the ordinary. Meanwhile, an XMRig cryptocurrency miner or other unwanted program is quietly running in the background of the victim’s Windows computer.
Trends
While searching for these particular fake Flash updates, we noticed Windows executables file names starting with AdobeFlashPlayer__ from non-Adobe, cloud-based web servers. These downloads always contained the string flashplayer_down.php?clickid= in the URL. We found 113 examples of malware meeting these criteria since March 2018 in AutoFocus. 77 of these malware samples are identified with a CoinMiner tag in AutoFocus. The remaining 36 samples share other tags with those 77 CoinMiner-related executables. See Appendix A for the full list of the file hashes.
Appendix B lists 473 file names and URLs for these fake Flash updates from March 25th, 2018 through September 10th, 2018.