Bitdefender has released new research highlighting a rapid increase in YouTube stream-jacking attacks.
The attacks involve either re-directing followers of a popular channel to one run by cybercriminals that closely mimics the real channel, or, a cybercriminal taking full control of the real channel.
The goal of YouTube stream-jacking is usually monetary; scamming followers of popular channels or personalities into sending cryptocurrency. For example, a message to send a small amount of Bitcoin for a 2X return on the investment.
Key findings:
- The maximum number of subscribers of a hijacked account observed is nearly 10 million. The top 10 accounts have nearly 37 million subscribers.
- Across the top 10 The total number of subscribers from the top 10 hijacked channels is nearly 37 million.
- The maximum number of views of a hijacked account observed is more than 3.6 billion. The top 10 accounts have nearly 10.4 billion views.
- Most hijacked channels use a variation of the Tesla logo or the official logo; all top 10 hijacked accounts involved the Tesla brand.
- The median number of subscribers on a channel is 2,260.
- The median number of view counts on a channel is 211,820.
- The number of distinct channels found was 1,190; and distinct broadcasted livestreams were 1,370.
- There are examples of hijacked channels that appear to belong to governmental entities.
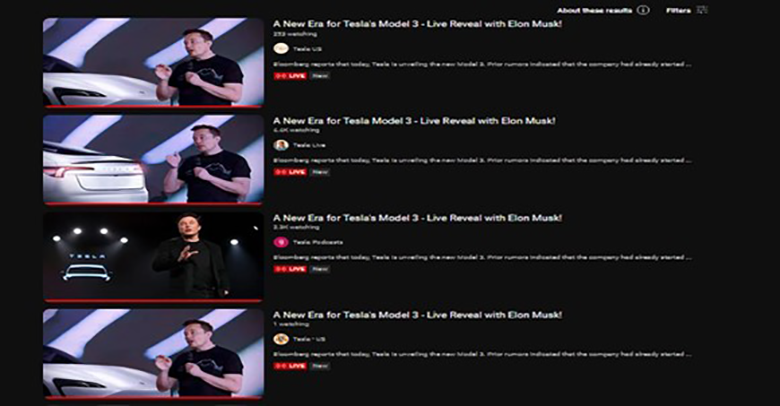
For channel impersonation attacks, cybercriminals set up YouTube livestream pop-ups in followers’ feeds that promote generally the same content as the real channel. The pop-up livestreams are usually looped re-broadcasts that contain an embedded scam either via backlink or QR code to a phishing or fraudulent website. Due to the amount of livestream pop-ups observed, the operation is most likely automated.
For account takeover attacks, a popular YouTube channel owner is sent a fake email, usually offering a collaboration opportunity or notice of copyright infringement. The channel owner is encouraged to download a file included in the email that is actually malware. Once the file is opened, the malware steals data from the computer allowing the attacker to access YouTube account credentials, even bypassing extra security measures such as two-factor authentication (2FA). Once accessed, the real owner is usually locked out.
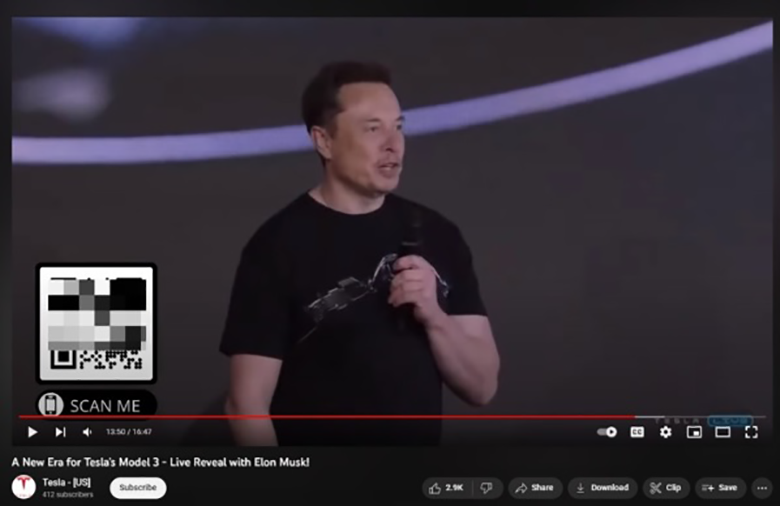
The titles are broadly similar, and examples include A New Era for Tesla’s Model 3 – Live Reveal with Elon Musk! or SpaceX Launch Hughes JUPITER 3 Mission! Elon Musk gives update on Starship. The comment sections of detected malicious livestreams are often disabled, but accounts that enable comments only do so for subscribers of 10 or 15 years, preventing users aware of the scam from commenting and alerting others. A common detail of livestreams is that attackers embed a QR code in portions of the video that leads to a phishing or fraudulent website.
Links propagated via hijacked YouTube channels promote a similar and well-known scam. It involves sending any amount of cryptocurrency (e.g., Bitcoin, Ethereum, USDT, Dogecoin, BNB, Shiba Inu) and promises to send double the amount back to the scammed person.

Bitdefender has also identified instances in which the audio and video looped in the livestream are deepfakes of Elon Musk, through which the hackers try to promote the importance of crypto and any event promoted in the referenced links. The deepfakes are of high quality and might seem genuine to the average viewer. During the analysis, Bitdefender also concluded some livestreams are view-boosted at the beginning of the broadcast, making it look more trustworthy. However, as soon as the view-boosting stops, numerous fraudulent livestreams drop to only one or two viewers.
The same applies to the number of subscribers. Even though there are enough occurrences of channels with low subscriber numbers, the median value seen in Bitdefender’s analysis is close to 2,300, which indicates potential subscriber boosting. The cybersecurity company has also deduced that all the channels investigated were created using automated software (phishing kits).
In most cases analysed, it seems that if the malicious activity is detected by YouTube, the actual channels are deleted altogether. This means that the legitimate owner of the channel will lose videos, playlists, views, subscribers, monetisation and everything that goes beyond the YouTube channel itself while still being related, unless talks are undertaken with YouTube.
Tips to protect YouTube users:
- Scrutinise videos with click-bait titles that encourage you to invest in crypto or promise hefty returns in Bitcoin investments.
- If it sounds too good to be true, it probably is. Stop and think before clicking on links you see in the description of videos.
- Never scan QR codes you see in videos promoting free crypto giveaways.
- Closely inspect the channel for suspicious activity such as missing or hidden videos.
- Pay close attention to the comment section in videos or livestreams; if it is closed it could be a sign of compromise.
- Use a security solution with anti-phishing technology that detects and blocks phishing attempts before they can damage your finances and identity.
Tips to protect YouTube channel owners:
- Ensure your account is set up using a unique and strong password. Never recycle passwords and consider a dedicated password manager service to help generate and manage secure passwords across all your online accounts.
- Enable additional layers of security such as 2FA or multi-factor authentication (MFA).
- Use caution when interacting with links you see in the comment section of your videos.
- Install a security solution to protect against phishing and malicious attacks.
- Immediately contact the platform’s support team to report suspicious activity or if you have been logged out of your account.
- Periodically review the list of individuals who have access to your YouTube channel, ensure that only necessary users have access, and limit permissions based on roles and responsibilities.
- Review the list of third-party applications connected to your account, remove any apps you don’t use and only keep those that are trustworthy and essential for your channel.
- Consider using digital identity protection services, which monitor the web for any data breaches involving your information. If your data is compromised, promptly change the passwords of the affected accounts.
- Practice good password hygiene by changing your YouTube password account every three months.
The full report can be viewed here.





