
Devices widespread across critical infrastructure sectors, highlighting the need for heightened security measures
Connecting unprotected critical infrastructure components to the internet carries with it unacceptable risks that industrial enterprises must make themselves aware of.
That may sound like an obvious statement, but it’s becoming increasingly clear that many organizations aren’t heeding the warnings from researchers about exposing misconfigured web-based interfaces online and mitigating control system software and firmware vulnerabilities in a timely fashion.
Relatively simple configuration mistakes such as not setting a password—or leaving default passwords in place—for devices can put infrastructure that monitors critical systems within reach of script kiddies as well as advanced attackers. Online tools, such as the Shodan internet search engine, can quickly enumerate specific types of machines connected to the internet, and in an instant, eradicate an organization’s belief that a device’s specific IP address won’t be found among tens of millions of others. It will.
The vulnerability in a nutshell
Claroty’s latest research into Ovarro’s TBox remote terminal units (RTUs) exposed several vulnerabilities that fit into this scenario. We also found other vulnerabilities that an advanced attacker could use to bypass existing protections in order to access devices and either disrupt them or execute code. Ovarro has patched all of the vulnerabilities in TBox firmware version 1.46 and TWinSOft version 12.4, and all users are urged to update immediately, or remain vulnerable to cyber attack.
The risks associated with these flaws threaten not only affect the integrity of automation processes, but also, in some cases public safety. Using these security shortcomings, we were able to find web-based interfaces, similar to HMIs, that monitor process levels and other industrial activity. We’ve seen in the past what could go wrong when such an interface is exposed to the internet without adequate security; the fact such interfaces are exposed online removes many barriers to entry for adversaries of all types.
This was probably best illustrated through a May 2020 incident when Palestinian hackers accessed control systems within Israel’s water infrastructure, with intent to raise the level of chlorine in the water supply. Israel’s CERT and Claroty researchers determined that these systems were not password-protected and were easy pickings for any attention-seeking or advanced adversary.
How common are the Ovarro devices?
RTUs are increasingly connected industrial assets that exchange telemetry with SCADA systems or distributed control systems. Ovarro is a leader in this space, and its TBox RTUs are prevalent in critical infrastructure, specifically in the water, power, oil & gas, transportation, and process industries, enabling remote control and monitoring of applications and processes.
According to Ovarro, TBox is a secure and powerful RTU solution for remote automation and monitoring of critical assets. In other words, it allows users to control and monitor remote processes via a dedicated web interface similarly to how a HMI controls a PLC, in one packed platform.
The Claroty Research Team early last year took a comprehensive look at the security of TBox RTUs, and found critical vulnerabilities that, if exploited, allow attackers to crash these devices or remotely execute code.
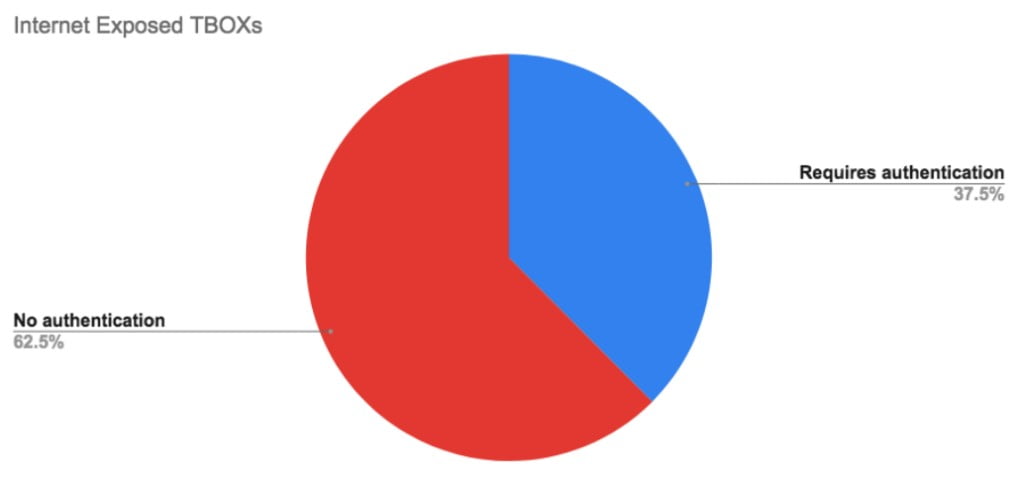
We used open source intelligence sources such as Shodan to compile some statistics on the availability of these devices online. Of all the internet-connected TBox RTUs we found online, only 37% had some sort of authentication protecting the device.
The following graph describes the Internet-facing HTTP service running on TBox devices that are directly accessible via the Internet. These HTTP services run the HMI web interface. As we can see, 62.5% don’t require authentication and therefore can enable any visitor to this service to control the RTU in hand or read data presented in the custom HMI panel configured on the device.
Specifics of the investigation
Claroty conducted its analysis of TBox on the LT2-530, version 1.44 build 485, and TWinSoft engineering software version 12.2.1, build 1545. The TBox RTU uses a default proprietary Modbus protocol for communication; SSH may be enabled for uploading files to the RTU and for firmware updates.
In its research, the Claroty Research Team was able to bypass and exploit vulnerabilities in each of these communication channels, eventually executing code remotely on the RTU regardless of any security mechanisms enabled.
Code Execution Through Update Packages
Attacks against the TBox RTU required targeting Modbus and eventually using update packages for code execution. TBox’s custom Modbus protocol implements updates using ipk packages, which are uploaded to a temporary file before an update command with the ipk file name is sent to the RTU where it is extracted to a directory. Claroty was able to modify the update package file before it’s sent to the RTU, writing any file to any location on the RTU including malicious executables that would launch when TBox restarts.
Denial of Service through Modbus File Access
The proprietary Modbus protocol handles a number of file operations, including read, write, and remove. The main RTU software, running as root, handles file access. We were able to override the RTU main configuration file, and either change or delete it, making it unstable until a root access user restores the configuration.
Modbus RTU Reset, Memory Corruptions
Prior to patching, TBox software running on the RTU would assume any Modbus frames it receives are valid. A specially crafted Modbus packet crashes the main program.
Bypassing Global/Enhanced Protection
Researchers were also able to bypass Global/Enhanced protection features in TBox, which is intended to limit file access; to do so we were able to decrypt passwords from communication between the RTU and engineering software, as well as bypass protections using a configuration read.
Affected Products:
- TBoxLT2 (all models)
- TBox MS-CPU32
- TBox MS-CPU32-S2
- TBox MS-RM2 (all models)
- TBox TG2 (all models)
- All versions prior to TWinSoft 12.4 and prior to TBox Firmware 1.46
TWinSoft version 12.4 and TBox firmware version 1.46 mitigate these vulnerabilities.
CISA also recommends minimizing the exposure of these devices to the internet, isolating control system networks and devices from business networks, and using VPNs for remote access.
CVE Information
- CVE-2021-22646
CWE-94 Improper Control of Generation of Code (Code Injection)
CVSS v3 Score: 8.8
This vulnerability and CVE-2021-22648 were the most severe among the vulnerabilities uncovered by Claroty researchers. With CVE-2021-22646, an attacker can exploit an ipk package update generated in TwinSoft engineering software to run malicious code in TBox. - CVE-2021-22648
CWE-732 Incorrect Permission Assignment for Critical Resource
CVSS v3 Score: 8.8
This vulnerability was found in the TBox proprietary Modbus file access functions that allow an attacker to read, alter, or delete a configuration file. - CVE-2021-22642
Uncontrolled Resource Consumption CWE-400
CVSS v3 Score: 7.5
A specially crafted Modbus frame can be used to crash a TBox system. - CVE-2021-22640
Insufficiently Protected Credentials CWE-522
CVSS v3 Score: 7.5
An attacker can decrypt the login password by communication capture and brute force attacks. - CVE-2021-22644
Use of Hard-Coded Cryptographic Key CWE-321
CVSS v3 Score: 7.5
TWinSoft uses a custom hardcoded user and cryptographic hardcoded key.






