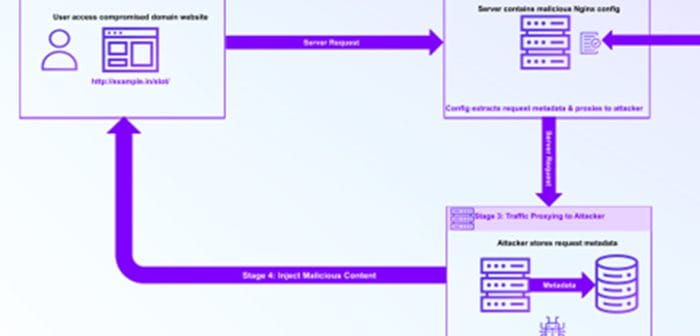
Featured
FeaturedBrowsing: Information Security

One of the world’s biggest manufacturer for electronics and electrical products, Mitsubishi Electric revealed that they were hacked, and found…
P&N bank has been involved in a data breach resulting in the exposure of customer information from the bank’s CRM…

VMware Carbon Black has released findings from its most recent retail cybersecurity report. ‘Tis the season for cyberattacks, particularly when…

Asterisk Information Security is pleased to announce the appointment of Drew Hamilton to the role of Security Consultant. Drew joins…
Survey of more than 1,000 individuals in Australia reveals cybersecurity knowledge and behaviour leaves room for improvement ESET has released…

July 2020 looms, and like impending doom, the pressure keeps mounting while no solution seems viable. As an organisation in…

Over the past 15 years, the Payment Card Industry Data Security Standard (PCI DSS) has evolved, grown, and put forth…

The United States continues to have complete dependence on information technology deployed in critical systems and applications in both the…

Kasada has announced that it closed its $7 Million Series A round, which includes funding from its newest investor In-Q-Tel, Inc.…

The National Cybersecurity Center of Excellence (NCCoE) is excited to announce the release of the new draft project description, Validating…