Overview
The second quarter of 2018 saw a continuation of trends we observed in the first quarter — increasingly diverse payloads in malicious emails, pervasive social engineering and growth in many areas of email fraud, increases in social media support fraud, and more. However, we also saw ransomware re-emerge as an email-based threat, albeit at lower volumes than during 2016 and 2017.
Among the key takeways from Proofpoint’s Q2 Threat Report:
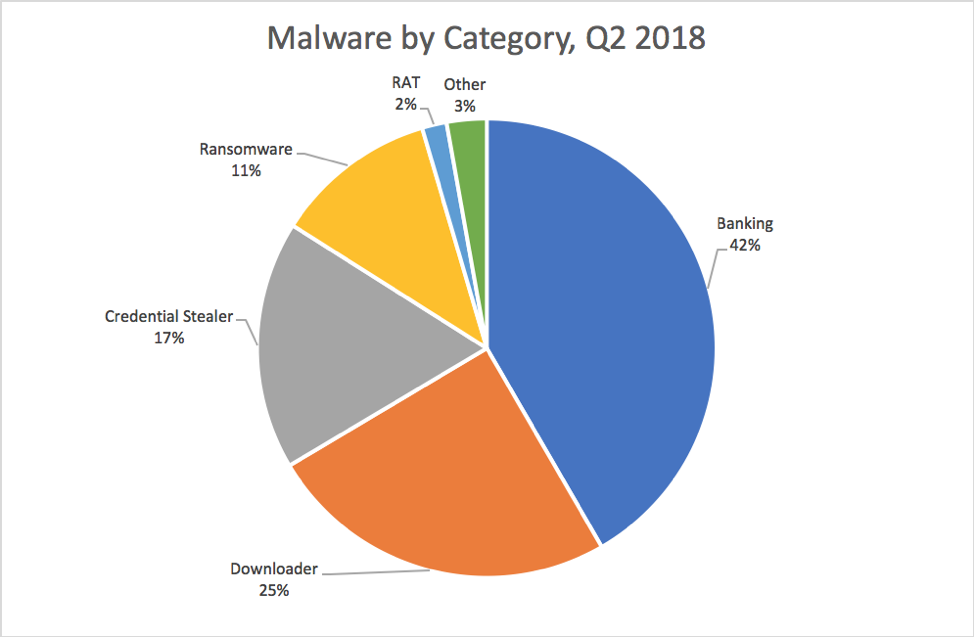
After being nearly absent from malicious email campaigns in the first quarter, ransomware returned with GandCrab, Sigma, and GlobeImposter ransomware all appearing in numerous campaigns. However, ransomware only accounted for 11% of observed malicious email volume, trailing behind banking Trojans, downloaders, and credential stealers. Notably, remote access Trojans (RATs), while comprising only 2% of malicious email payloads, doubled their relative footprint vs. Q1.
Email fraud, also known as business email compromise or BEC, increased globally. Targeted organizations received, on average, 26% more email fraud messages vs. Q2 and 87% more than they received in Q2 2017. While companies of all sizes were targeted equally by email fraud, some industries such as retail, healthcare, and government all experienced larger increases in BEC activity than their counterparts.
Exploit Kits and Web-Based Attacks
As exploit kit activity continued to decline, web-based social engineering attacks quickly moved to fill the void. These schemes, particularly those using fake antivirus and browser plugin updates grew 500% vs. Q1.
Another type of web-based attack known as “cryptojacking”, in which CoinHive software is used to mine cryptocurrency using visitor CPU cycles, also increased dramatically, increasing 460% from Q1.
Social Media
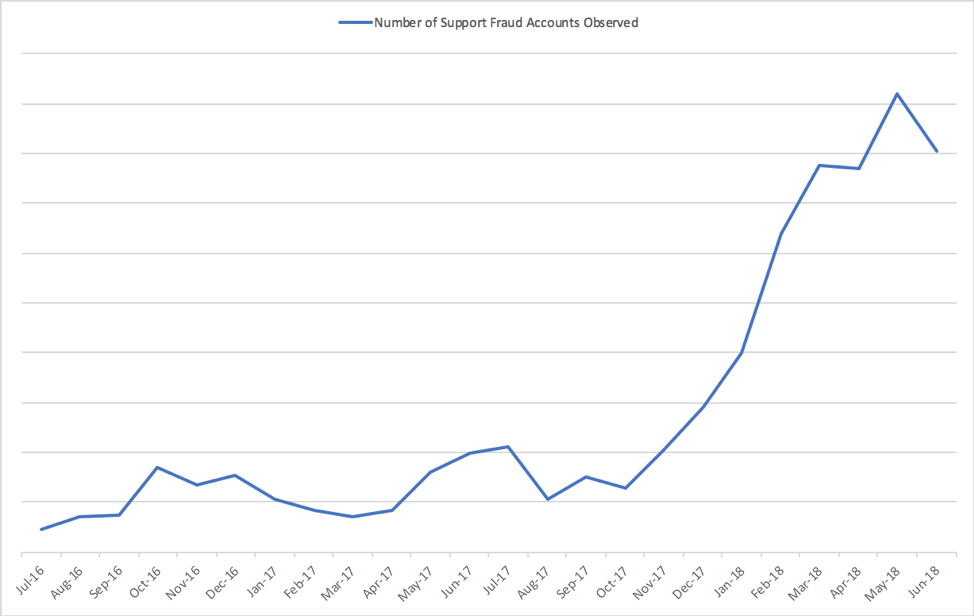
Even after an explosion of new support fraud accounts in Q1, social media support fraud continued to expand in Q2. Also known as “angler phishing,” social media support fraud increased another 38% over Q1. (Figure 2).
We also detected the first increase in social media link spam in several quarters, in an apparent reversal of a trend away from phishing and spam links on social channels.
Proofpoint Recommendations
The Q2 Threat Report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your company and brand in the coming months:
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks, and criminals continue to find new ways to exploit the human factor. Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Build a robust email fraud defense. Highly targeted, low-volume email fraud attacks often have no payload at all and are thus difficult to detect. Preventing email fraud requires a multilayered solution that includes email authentication and domain discovery, as well as dynamic classification that can analyze the content and context of emails, stopping display-name and lookalike-domain spoofing at the email gateway.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand. Look for a comprehensive social media security solution that scans all social networks and reports fraudulent activity.
For more information, download the complete Q2 2018 Threat Report.