The attacks are aimed at Linux devices that run one of the following products, which all have relatively new vulnerabilities that are exploited by the FreakOut malware if the products have not being patched:
- TerraMaster TOS (TerraMaster Operating System), a well-known vendor of data storage devices
- Zend Framework, a popular collection of library packages, used for building web applications
- Liferay Portal, a free, open-source enterprise portal, with features for developing web portals and websites
If successfully exploited, each device infected by the FreakOut malware can be used as a remote-controlled attack platform by the threat actors behind the attack, enabling them to target other vulnerable devices to expand their network of infected machines. The FreakOut malware’s capabilities include port scanning, information gathering, creation and sending of data packets, network sniffing, and the capability to launch DDoS and network flooding attacks.
The attack exploits the following CVE’s :
- CVE-2020-28188 – released 28/12/20 – TerraMaster TOS
- CVE-2021-3007 – released 3/1/21 – Zend Framework
- CVE-2020-7961 – released 20/03/20 – Liferay Portal
Patches are available for all products impacted in these CVEs, and users of these products are advised to urgently check any of these devices they are using and to update and patch them to close off these vulnerabilities.
FreakOut’s Impact
Based on Check Point’s code review, the attacker can use systems compromised by FreakOut for further malicious activity, such as crypto-mining, spreading laterally across corporate networks, or launching DDoS attacks on other organisations’ networks, which can shut down the entire systems infected.
The research found evidence from the attack campaign’s main C&C server that around 185 devices had been hacked.
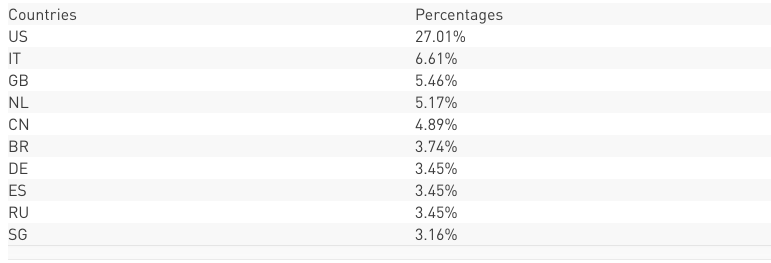
Between January 8th – 13th, over 380 attack attempts against Check Point customers were observed, and all of them were blocked. According to the global network of threat sensors, the geographies that were most targeted were North America and Western Europe.
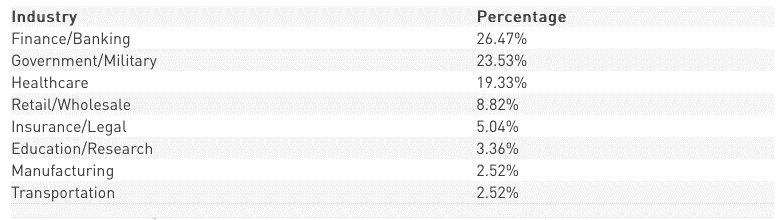
The industry sectors´ most targeted were finance, government and healthcare organisations.
Security tips to remain protected
- Strongly recommend users check and patch their servers and Linux devices in order to prevent the exploitation of such vulnerabilities by FreakOut
- Intrusion Prevention Systems (IPS) prevent attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking threat. Updated IPS helps your organisation stay protected.
- Endpoint protections: Conventional signature-based Anti-Virus is a highly efficient solution for preventing known attacks and should definitely be implemented in any organisation, as it protects against a majority of the malware attacks that an organisation faces.
- Comprehensive advanced endpoint protection at the highest security level is crucial in order to avoid security breaches and data compromises
Conclusion
“FreakOut” is an attack campaign that exploits three vulnerabilities, including some newly released, to compromise different servers. The threat actor behind the attack, named “Freak”, managed to infect many devices in a short period of time, and incorporated them into a botnet, which in turn could be used for DDoS attacks and crypto-mining. Such attack campaigns highlight the importance and significance of checking and protecting your assets as an on-going basis. This ongoing campaign can spread quickly, as we have seen.
For the full technical details of this research visit: https://research.checkpoint.com/