
By Unit 42, Palo Alto Networks.
The ongoing transition to cloud platforms has meant that more sensitive data is stored in the cloud, making it more tempting for adversaries to exploit. When it comes to securing the cloud, identity is the first line of defense. Without proper identity and access management (IAM) policies in place, an organization can pay for any number of security tools – but comprehensive security will never be possible.
To understand how IAM policies affect organizations’ cloud security posture, we analyzed 680,000+ identities across 18,000 cloud accounts from 200 different organizations to understand their configuration and usage patterns. The results of our research were shocking.
Nearly all organizations we analyzed lack the proper IAM management policy controls to remain secure.
These misconfigured IAM policies open the door for what Unit 42 defines as a new type of threat: Cloud Threat Actors. We define a cloud threat actor as “an individual or group posing a threat to organizations through directed and sustained access to cloud platform resources, services or embedded metadata.” We observe that they have begun to employ a fundamentally different set of tactics, techniques and procedures (TTPs) that are unique to the cloud – such as taking advantage of the ability to perform both lateral movement and privilege escalation operations simultaneously.
Throughout the pandemic, there were significant expansions of cloud workloads overall. Organizations increased their cloud usage – with a dramatic surge in the number of organizations that host more than half their workloads in the cloud (see Figure 1 below).
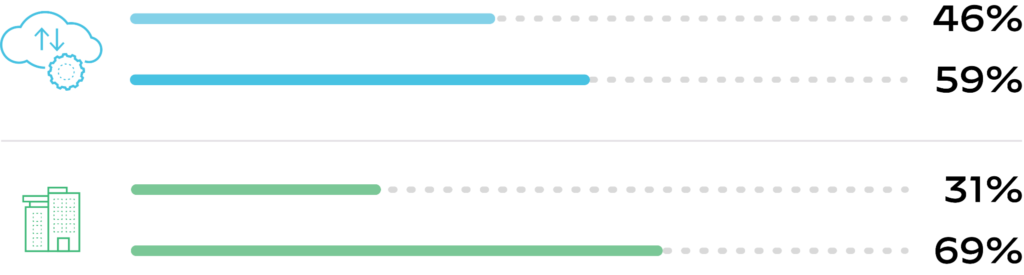
Figure 1. Percent change in cloud workloads since 2020, where blue represents cloud workload volumes and green represents organizations hosting more than half their workloads in the cloud.
When attackers take advantage of misconfigured or overly permissive identity access controls, they don’t need to figure out how to pull off a technically complex compromise. Instead, they can simply gain access to resources as if they have a right to them.
Threat actors are hungry to target organizations that lack proper IAM controls, and pairing this hunger with an increased usage of cloud platforms creates a new kind of threat – one that is more sophisticated yet requires less effort to execute. The question turns to why and how this is possible.
Key Findings From Unit 42’s Cloud Threat Report: IAM The First Line of Defense
Let’s address the “why” first by explaining some of the key statistics we uncovered:
- Password reuse: 44% of organizations allow IAM password reuse.
Weak passwords (<14 characters): 53% of cloud accounts allow weak password usage.
Cloud identities are too permissive: 99% of cloud users, roles, services, and resources were granted excessive permissions which were ultimately left unused (we consider permissions excessive when they go unused for 60 days or more).
Built-in cloud service provider (CSP) policies are not managed properly by users: CSP-managed policies are granted 2.5 times more permissions than customer-managed policies, and most cloud users prefer to use built-in policies. Users are able to reduce the permissions given, but often don’t.
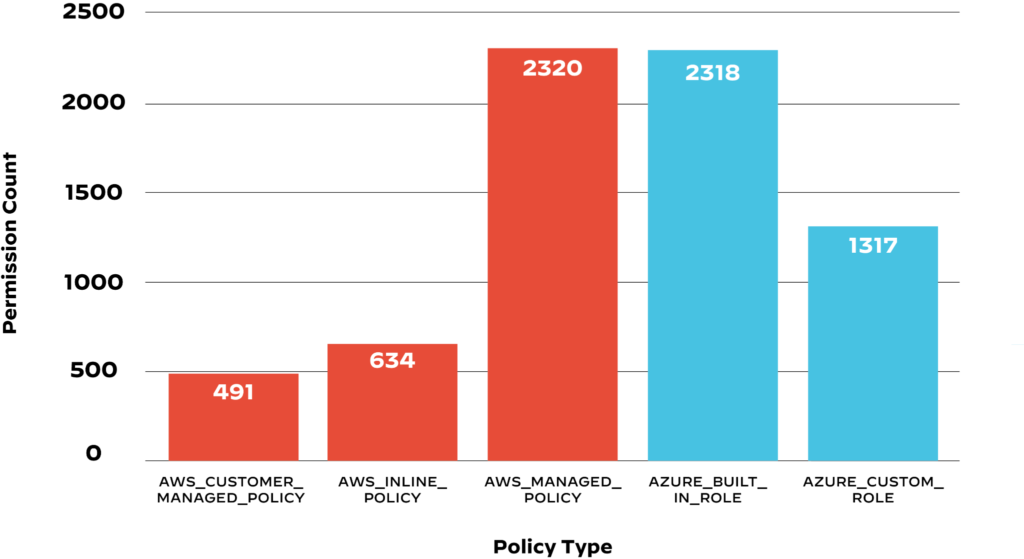
Figure 2. Average number of permissions granted by each policy type. CSP-managed policies (AWS_MANAGED_POLICY and AZURE_BUILT_IN_ROLE) grant 2.5 times more permissions than customer-managed policies.
With organizations allowing excessive permissions and overly permissive policies, attackers are too often welcomed into an organization’s cloud environment with keys to the kingdom. Most organizations are unprepared for an attack through the exploitation of weak IAM policies. Adversaries know this as well; they target cloud IAM credentials and are ultimately able to collect these credentials as part of their standard operating procedures. Case in point, they’re leveraging new TTPs unique to cloud platforms that organizations need to be aware of in order to implement a strategy to protect themselves.
Cloud Threat Actor Index for Defense Against IAM Cloud Threats
To help organizations defend themselves against this threat, we created an industry-first Cloud Threat Actor Index that can be found in our report, which charts the operations performed by actor groups that target cloud infrastructure. These charts detail the TTPs of each cloud threat actor, allowing your security team and wider organization to evaluate your strategic defenses and build the proper monitoring, detection, alerting and prevention mechanisms.
The Cloud Threat Actor Index highlights the top actors targeting cloud infrastructure, as well as nation-state actors that have been known to use the cloud to conduct attacks. Below is a preview of the top cloud threat actors that we’ve indexed. We charted their operations in our report, sorted by prevalence.
- TeamTNT: The most well-known and sophisticated credential targeting group.
WatchDog: Considered to be an opportunistic threat group that targets exposed cloud instances and applications.
Kinsing: Financially motivated and opportunistic cloud threat actor with heavy potential for cloud credential collection.
Rocke: Specializes in ransomware and cryptojacking operations within cloud environments.
8220: Monero mining group, purportedly elevated their mining operations by exploiting Log4j in December 2021. - Top Advanced Persistent Threats Utilizing and Targeting Cloud Infrastructure
APT 28 (Fancy Bear)
APT 29 (Cozy Bear)
APT 41 (Gadolinium)
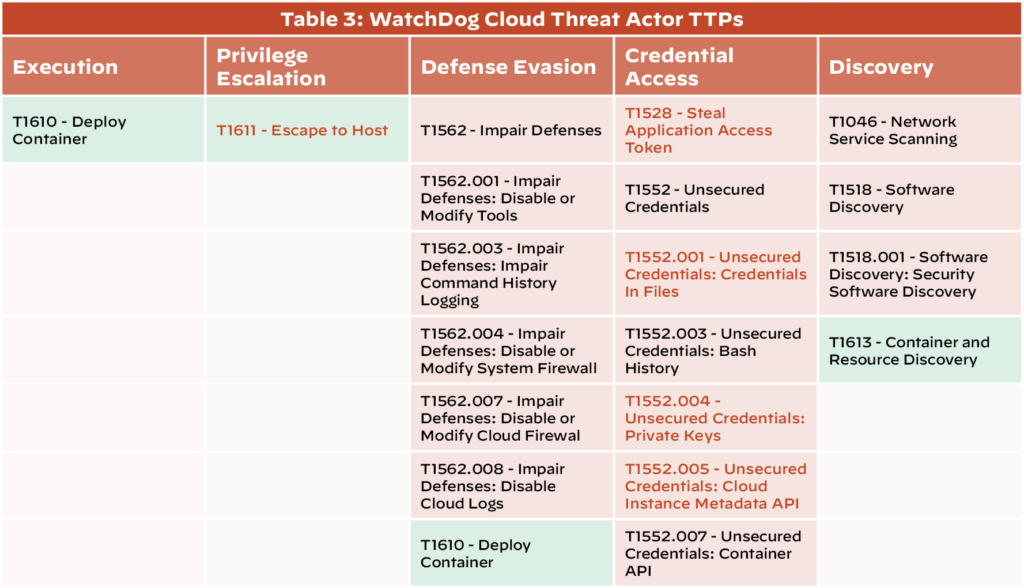
Figure 3. WatchDog Cloud Threat Actor TTPs. The red background denotes TTPs specific to cloud platforms, whereas the green background denotes TTPs which are container-platform specific. TTPs in red font denote operations that can lead to the wider compromise of cloud operations.
Defense Against Cloud Threats
Proper IAM configuration can block unintended access, provide visibility into cloud activities and reduce the impact when security incidents occur. In particular, we recommend that organizations defend against threats that target the cloud in the following ways:
Cloud-Native Application Protection Platform (CNAPP) suite integration.
Harden IAM permissions.
Increase security automation.





