
For most Australians, lockdowns and restrictions have changed education forever. Not only are educational staff, academia and students forced to continue online learning, but the sector is also experiencing a huge spike in cyberattacks. In fact, Australia is the 4th most targeted country in the world.
Check Point Research (CPR) found the education sector to have the highest volume of cyber attacks for July, with an average of 3,934 attacks documented per organisation, impacting schools, universities and research centres each week, marking a 17% increase from the first half of 2021.
Cybercriminals are capitalising on the short-notice shift back to remote learning due to the Delta variant and targeting staff, students and academics of schools, universities and research centres who use their personal devices to log in. This reality means that it’s never been more important to raise awareness for cyber safety to protect against cyber threats and attacks.
Key findings:
- Australian education sector saw a 17% increase in cyberattacks, and an average of 3,934 attacks in July, compared to the first half of 2021
- Global education sector saw a 29% increase in cyber attacks, and an average of 1,739 attacks a week, during the same period
- Top 5 most attacked countries were India, Italy, Israel, Australia and Turkey
Most Targeted Countries: India, Italy, Israel, Australia and Turkey
The table below shows the number of weekly cyber attacks in July on the education sectors for India, Italy, Israel and Australia, as well as the percent increases compared to the first half of 2021.
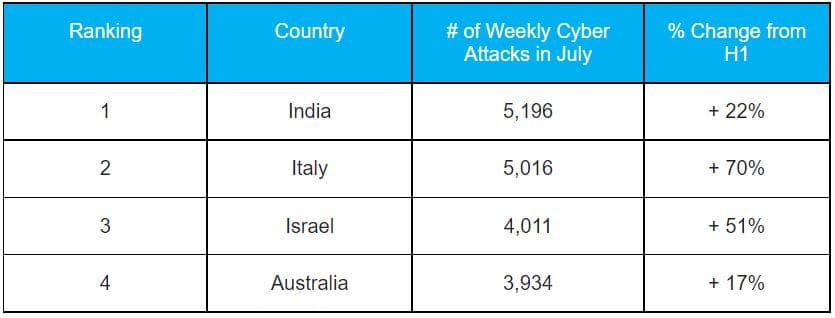
Figure 1: Weekly attacks per organisations by country (July 2021 compared to first half of 2021)
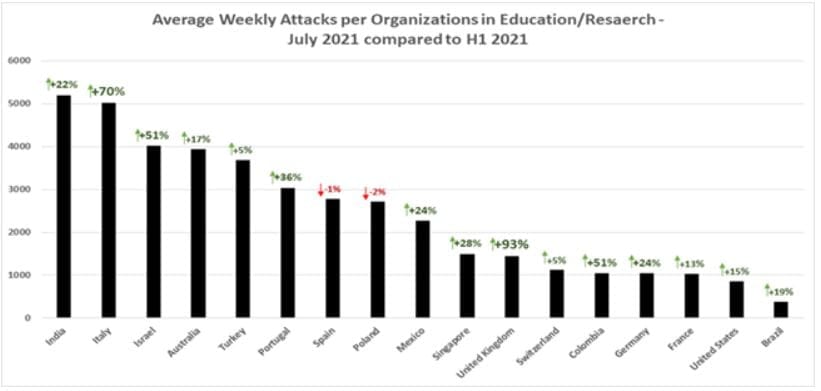
In more than half of the countries studied by CPR, the education sector is the most attacked sector, and in 94% of them, the education sector is in the top three most attacked sectors.
Cyber Safety Tips for Academia, Staff and Students·
- Strengthen passwords.Passwords matter – it is a good idea to review and strengthen passwords that you use for logging onto remote resources, such as email or work applications.
- Be phishing-aware: be wary of clicking on links that look in any way suspicious and only download content from reliable sources that can be verified. Remember that phishing schemes are a form of social engineering so if you receive an email with an unusual request, check the sender’s details carefully to make sure that you are communicating with colleagues, not cyber criminals.
- Reduce attack surfaceA common approach in information security is to reduce the attack surface. For endpoints, you need to take full control of peripherals, applications, network traffic, and your data. You need to encrypt data when it is in motion, at rest, and in use. It is also important to make sure you enforce your corporate policies to achieve endpoint security compliance
- Use Anti-ransomware.This technology allows you to detect signs of ransomware and uncover running mutations of known and unknown malware families by using behavioral analysis and generic rules
- Contain and remediate. Contain attacks and control damage by detecting and blocking command and control traffic and prevent the lateral movement of malware by isolating infected machines. You can then remediate and sterilise your environment by restoring encrypted files, quarantining files, kill processes, and sterilising the full attack chain.
Download the full report here.





