
Written by Ben Higgins, Edward Wu, and Jonathan Wrolstad.
In November 2022, members of the ExtraHop Detections Research and Data Science teams picked up on a device in an organisation’s network environment that was making suspicious outbound connections to a confirmed Cobalt Strike command and control (C2) server.
Cobalt Strike is a legitimate penetration testing and attack simulation platform used by red teams, but over the past three to four years threat actors including Cozy Bear and the Conti, Black Basta, and Royal ransomware gangs have used it as a tool in their arsenal. Specifically, they deploy Cobalt Strike to establish communications with a C2 server once they’ve gained access to an organisation’s environment. Attacks leveraging Cobalt Strike frequently foreshadow ransomware.
The C2 communications that we detected in early November using the ExtraHop Reveal(x) network detection and response (NDR) platform, combined with other data and threat intelligence sources, strongly suggested that a malicious actor had breached the organization’s perimeter defenses and was potentially looking to take a number of actions, including network reconnaissance, lateral movement, and credential theft–with the possible intent to deploy ransomware and/or exfiltrate data.
In this threat analysis report, we share our findings and detection methodology to help cybersecurity practitioners identify Cobalt Strike in their environments. We also describe how we discovered the malicious activity using ExtraHop Reveal(x), and we explain the benefits and impact of detecting this attack in its early stages.
The Detection
On November 9, 2022, an ExtraHop Reveal(x) sensor monitoring an organization’s network picked up on unusual traffic patterns coming from an internal device (later identified as an employee laptop) that was making suspicious outbound connections to an external device with the IP address 194.165.16.90.
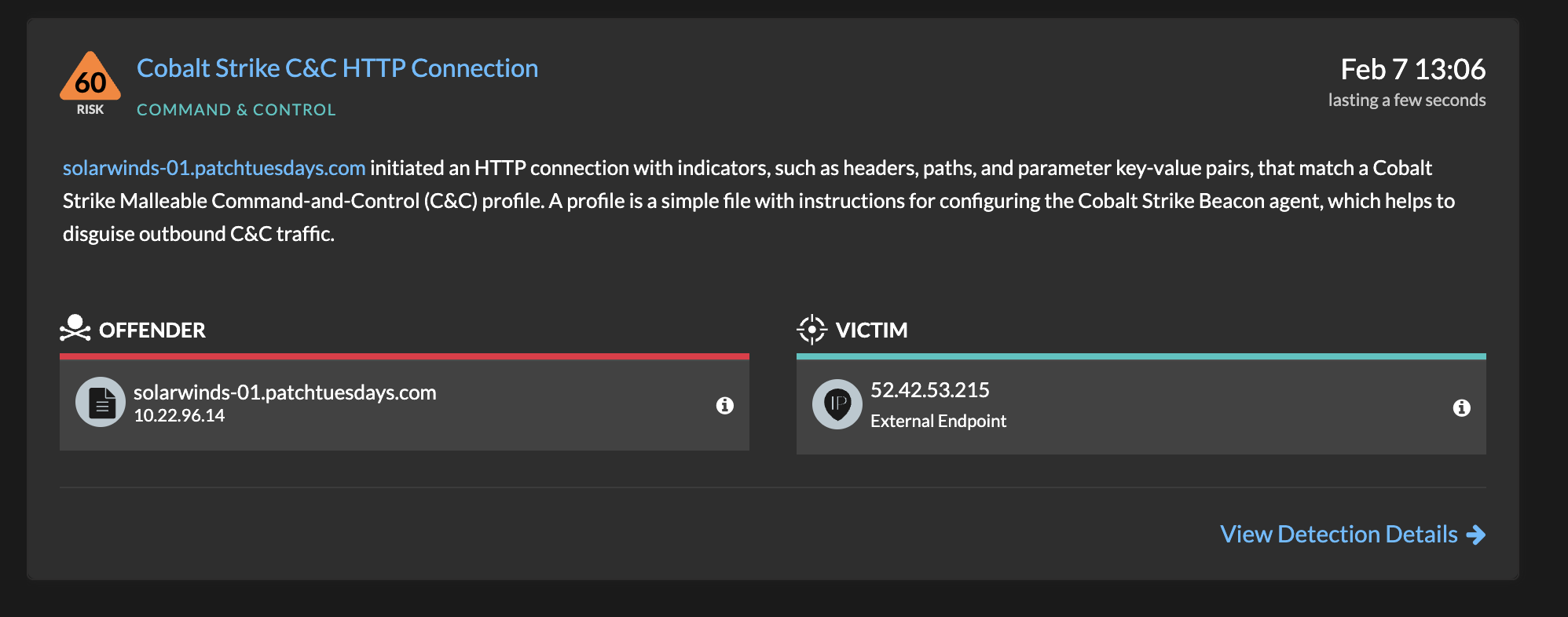
According to Censys, the external device had ports 22 (SSH), 53 (DNS), and 80, 443, 8080, and 8888 (all plain text HTTP) open. We noted that ports 80 and 8080, which usually communicate over plain text HTTP, were in this case using HTTPS to communicate with the internal device on the organization’s network, which was unusual.
The most convincing evidence came from our proprietary fingerprinting method, which the ExtraHop Threat Research team runs constantly against the internet and which flagged the external IP address as suspicious. Our fingerprinting method for detecting Cobalt Strike C2 servers probed ports 80, 443, 8080, and 8888, and all came back with a positive result. Furthermore, we knew the external IP address was hosting a Cobalt Strike C2 server because one of our researchers was able to download a beacon from it. Our beacon analysis suggested the downloads did not come from a legitimate, licensed copy of Cobalt Strike. Had the beacons come from a legitimate copy of the software, it would have been a stronger indication of red team usage, but in this case, because the beacons appeared to come from an unlicensed copy, it increased the likelihood that a malicious actor was using these tools rather than a red team.
The automated detection from Reveal(x), combined with our own active probing as well as internal and external threat intelligence sources, indicated the IP address belonged to an external device hosting a Cobalt Strike C2 server, and therefore, signaled a high-fidelity alert about a potentially very serious and fast-moving attack.
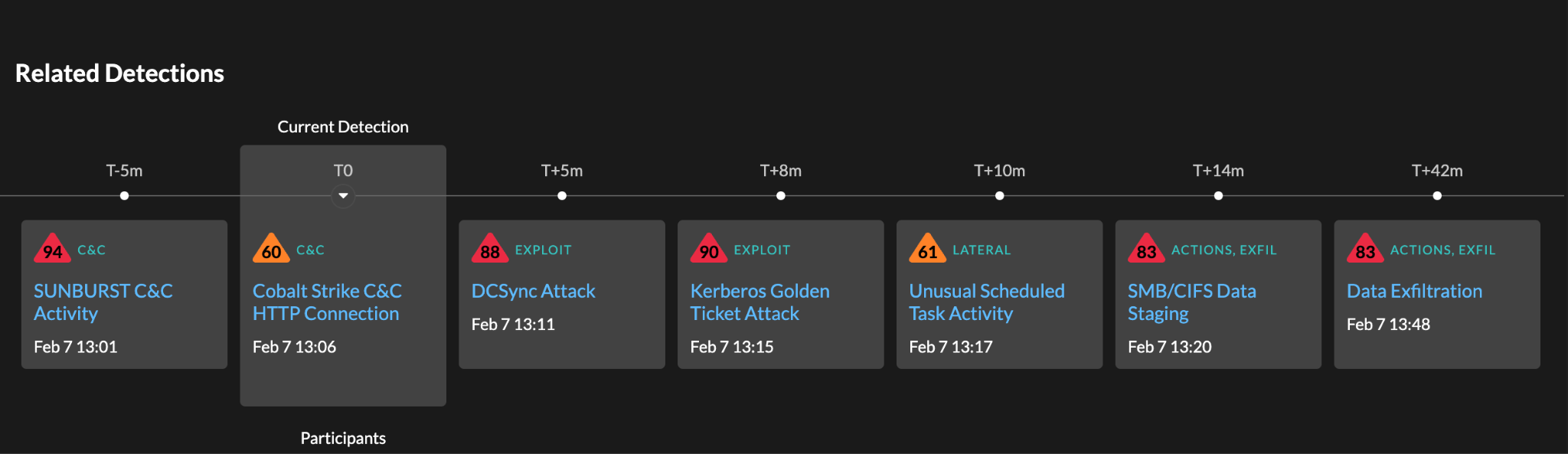
The Attack Chain
ExtraHop contacted the organisation about the detection, and the organization was then able to identify how the threat actor gained initial access: an end user who was logged into the organization’s network via a VPN received a phishing email with an HTML file. The end user clicked on the file, which triggered a malicious executable–several strong signals indicated it was likely Qakbot–to immediately download on the user’s machine. Qakbot (also known as Quakbot and QBot) allows attackers to conduct network reconnaissance, move laterally, and deliver payloads such as Cobalt Strike and Conti, ProLock and Egregor Ransomware. In this case, Qakbot led to the delivery of Cobalt Strike, which then established a link to a C2 server the very next day, signalling an attack that was likely to progress rapidly and likely to conclude with ransomware.
MITRE ATT&CK Tactics and Techniques Used in This Attack
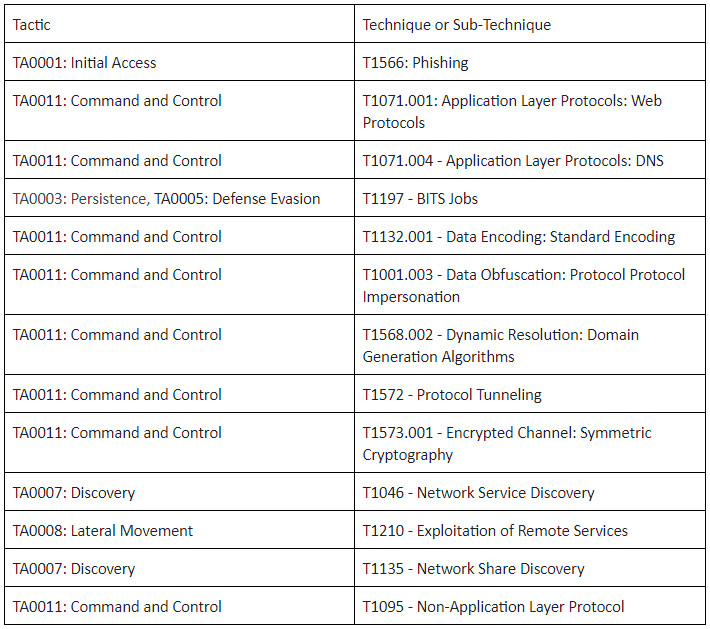
It is important to note that there were a number of significant security controls these sophisticated, stealthy attack tools managed to circumvent:
- VPN
- Firewall
- Intrusion Detection System (IDS)
- Email security
- Anti-virus software
The visibility that ExtraHop Reveal(x) provided into full network activity allowed us to quickly detect malicious behaviour. The early detection then allowed the organisation to stop an attack that was likely to progress rapidly and conclude with ransomware and/or data exfiltration scenarios.
Containment and Remediation
When the organisation became aware of the outgoing connections, its security team took a number of steps to contain and remediate the compromise, including disconnecting the affected device from the internet, changing account passwords and access control credentials, quarantining the device from the network, and removing the malware. The security team then assessed the scope of the compromise, eliminated the attacker’s presence, blocked access, closed attack vectors, and updated and augmented security controls to prevent similar future compromises. The organisation also continued to use ExtraHop Reveal(x) to monitor the network for suspicious behaviour.
Evasive Malware Requires Powerful Network Detection
Cobalt Strike has become a powerful adversarial tool because it delivers a full range of post-exploit capabilities via a single, integrated system and also because it employs so many techniques to evade detection. For example, Cobalt Strike can imitate the HTTP protocol for C2 communication while hiding the actual data in either an HTTP header, URI parameter, the transaction body, or appending it to the URI. Cobalt Strike can break large data sets into smaller chunks so as not to trigger data loss prevention systems during exfiltration. Cobalt Strike can encrypt task commands, shell code, configuration data, and data being sent to a C2 server. It can use custom C2 protocols that can be encapsulated in HTTP, HTTPs, and DNS, even as those custom protocols use their standard assigned ports, and it can do much, much more.
That’s why attacks leveraging Cobalt Strike tend to be serious. It’s also why organisations need NDR. Only NDR–and more specifically, Reveal(x) 360–can detect the highly covert, super subversive, network-level techniques attackers use to fly under the radar. We build behaviour-based detections for Cobalt Strike and other tools that catch the most subtle activities.
Even if it’s your last line of defence against sophisticated threat actors, ExtraHop Reveal(x) can still help you detect their attacks before IDS, AV, EDR and SIEM and before they lead to business impact.





