
The Australia India Institute has secured funding under the Australia–India Cyber and Critical Technology Partnership (AICCTP) to lead a new…

ThreatLocker has expanded its cybersecurity platform with new Zero Trust network and cloud access capabilities designed to reduce the impact…

Australian and allied cyber security agencies have warned that malicious actors are actively targeting organisations’ SD-WAN infrastructure by exploiting a…

The Telecommunications Industry Ombudsman (TIO) received 14,017 complaints between October and December 2025, a 3.6% increase on the previous quarter,…
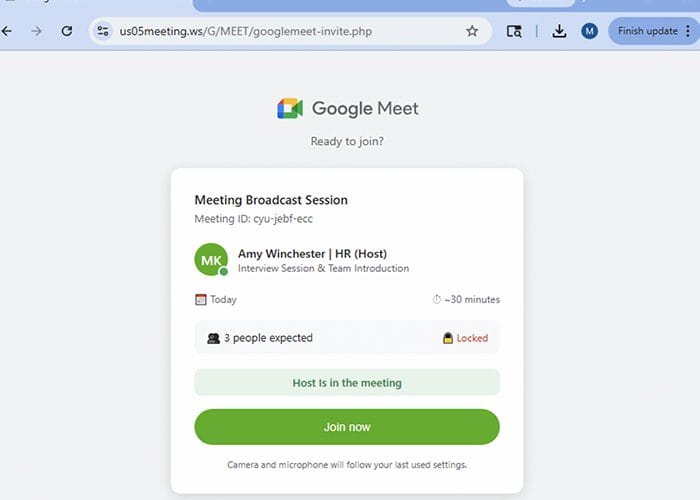
Netskope Threat Labs has identified a new phishing campaign using fake video conference invitations to deliver remote access tools into…

Optus continues to work through a mobile network software issue that has left around 35,000 customers without full service, according…

Over the last month, Barracuda threat analysts have investigated the following email threats targeting organisations and their employees: Tycoon phishing kit using…

A new report from BioCatch points to the explosive and exponential growth of scams all around the world. The research…

A sophisticated callback scam is underway where criminals are impersonating Australian Big Four banks in an attempt to extract money…

The Office of the Australian Information Commissioner (OAIC) has published regulatory guidance for age-restricted social media platforms and age assurance…

