Featured
FeaturedBrowsing: Information Security

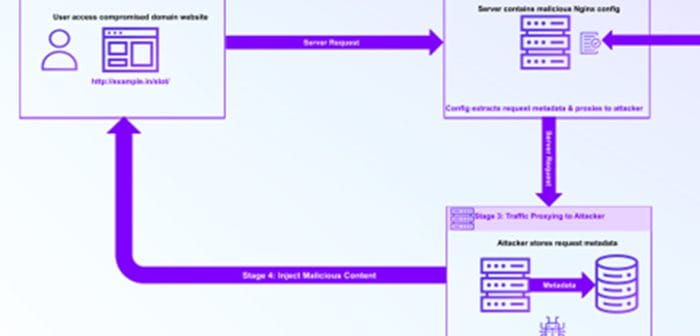
Bitdefender investigators have today announced the discovery of a sophisticated espionage campaign that targets air transportation organisations and government entities…

A third of the way through the calendar, and it seems 2020 is the year we accept a “new normal”.…

We missed timing this with World Password Day (May 7 – First Thursday of May) but took the opportunity to…

Global survey shows the average cost of recovery is US$1.4 million if organisations pay the ransom, US$730,000 if they don’t…

In a statement released late yesterday (12 May) Toll has confirmed data theft following a targeted cyber attack. With comments…

Cognitive dissonance prevails, unchanged behaviors create new online security concern LastPass by LogMeIn has released findings of its third Psychology…

SolarWinds has released the findings of SolarWinds IT Trends Report 2020: The Universal Language of IT. This year’s annual report…
ESET Internet Security has been picked as a Recommended product by CHOICE for the second year in a row. The…

Interview with Matt Hanmer, managing director for ANZ and regional director for South Pacific for Infoblox and Jasper Chik, Sales…

The Parliamentary Joint Committee on Intelligence and Security has completed its Review of the mandatory data retention regime, and is…