
Prevalence of Cryptomining Malware Jumped to 28%, Impacting a Quarter of ANZ Organisations Jon McGettigan, Fortinet’s regional director for ANZ…

Karan Khosla, Director of Privasec provides case study insight into the Privasec’s red-teaming operations. Hosting a Cyber Risk Meetup round-table…
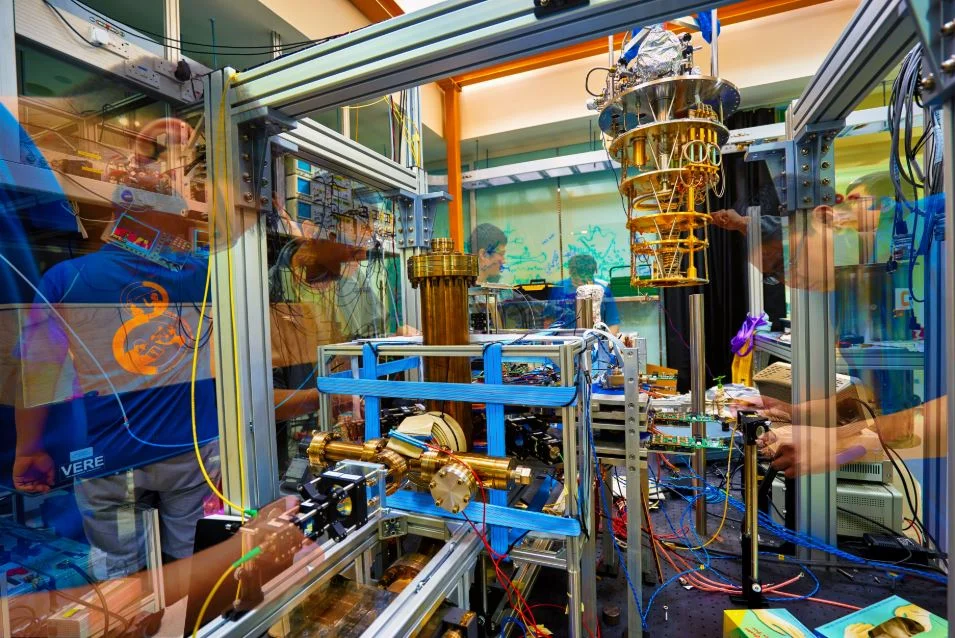
Special Report by Jane Lo, Singapore Correspondent Around the world, governments and companies are racing to build quantum computers that…

EU Cybersecurity Agency ENISA organised an international cybersecurity exercise Imagine this: It is a normal day at the airport. All…

FireEye has released research detailing how the malware TRITON works and was created. TRITON was identified late last year by…

The Office of the Australian Information Commissioner (OAIC) has confirmed it is in contact with the Australian Cyber Security Centre…

In this third article in our series about cyber insurance, we’re looking at two publicised examples of how a Cyber…

Mt. Gox, where are our bitcoins? Mark Karpeles bowed in front of the Japanese press with his eyes closed. He…

Talking of Offensive Individuals – Penetration Testers My love of hacking systems came from way back, before penetration testing was…

In this interview, Morry Morgan chats with Chris Gatford, Director & Founder of Hacklabs, speaking at the CIVSEC 2018 Congress and…

