
Cyber crime today is big business. Industry sources estimate it will cost the world a staggering US$6 trillion annually by…

Overview The second quarter of 2018 saw a continuation of trends we observed in the first quarter — increasingly diverse…

In this interview, we discuss how Data Mining techniques and machine learning algorithms can be extremely useful when applied in covert channel detection and…

NIST announces the release of Draft NISTIR 8214, Threshold Schemes for Cryptographic Primitives: Challenges and Opportunities in Standardization and Validation…

NIST is updating its guidance for transitioning to the use of stronger cryptographic keys and more robust algorithms by federal…

New 2019 Bitdefender Consumer product line dials up aggression against online crime Bitdefender has launches its 2019 consumer security product…

NIST seeks comments on Draft Special Publication (SP) 800-56B Revision 2, Recommendation for Pair-Wise Key-Establishment Using Integer Factorization Cryptography. This…

NIST’s newly released SP 800-71 Recommendations for Key Establishment Using Symmetric Block Ciphers addresses the protection of symmetric keying material…
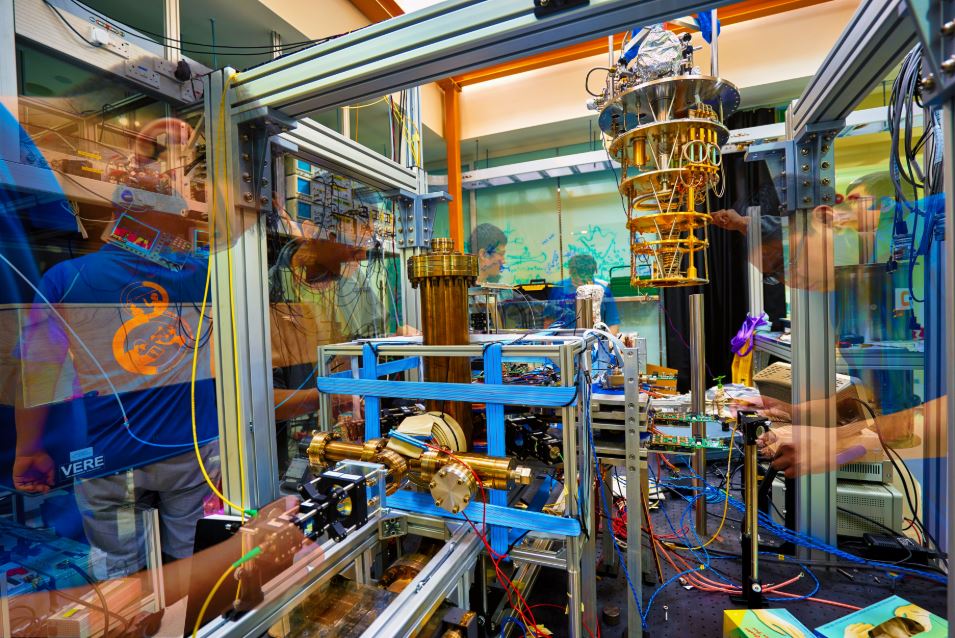
Special Report by Jane Lo, Singapore Correspondent Around the world, governments and companies are racing to build quantum computers that…

Early in 2018, Proofpoint researchers observed a rise in so-called “cryptocurrency giveaway scams.” The scams often target users of Ethereum…

