
Dragos has identified a shift from reconnaissance to operationally focused cyber activity across industrial infrastructure, alongside a sharp increase in ransomware activity affecting operational technology (OT) environments.
In its 2026 OT/ICS Cybersecurity Report and Year in Review, the company said adversaries are increasingly mapping entire industrial control systems rather than targeting isolated devices. The report, now in its ninth year, identified three new OT-focused threat groups and documented continued growth in ransomware targeting industrial organisations.
Dragos added AZURITE, PYROXENE and SYLVANITE to its tracking list, bringing the total number of monitored OT threat groups to 26, with 11 active in 2025.
SYLVANITE was observed acting as an initial access broker, exploiting vulnerabilities and handing off established footholds to VOLTZITE for deeper OT intrusions. The group was seen targeting US electric and water utilities, exploiting Ivanti vulnerabilities and extracting Active Directory credentials. AZURITE focused on long-term access and theft of operational data from engineering workstations across the United States, Australia, Europe and Asia-Pacific. PYROXENE conducted supply chain compromises and social engineering campaigns, targeting aviation, aerospace, defence and maritime sectors in the US, Western Europe and the Middle East.
The report also highlighted progression among established threat actors. ELECTRUM carried out destructive operations during 2025, including attacks on Ukrainian ISPs and attempts to affect operational assets at combined heat and power facilities and renewable energy systems in Poland. KAMACITE was observed mapping control loops across US infrastructure, scanning industrial components including HMIs and variable frequency drives. VOLTZITE, which shares technical overlaps with Volt Typhoon activity, was elevated to Stage 2 of the ICS Cyber Kill Chain after manipulating engineering workstation software and compromising cellular gateways to access pipeline operations.
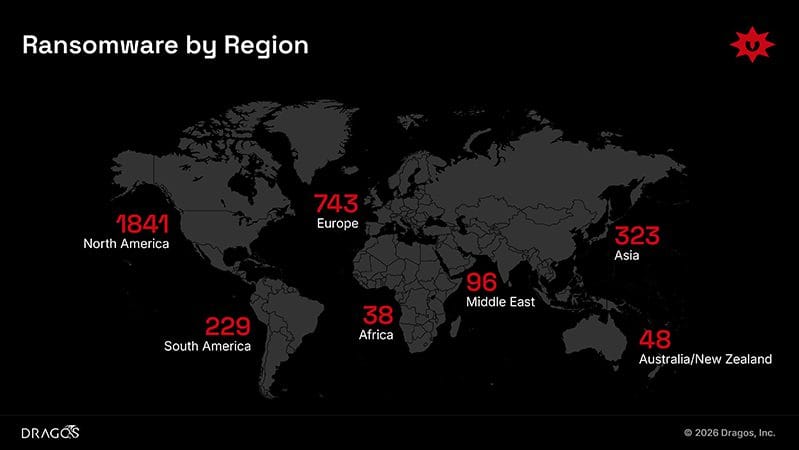
Ransomware remained the most disruptive threat category. Dragos tracked 119 ransomware groups targeting industrial organisations in 2025, up from 80 the previous year, representing a 49% increase in groups with reach into OT environments and a 64% year-on-year increase in overall attacks. More than 3,300 organisations were affected globally, with manufacturing accounting for over two-thirds of victims. The average dwell time for ransomware in OT environments was 42 days.
The report noted that many incidents are misclassified as IT-only events because OT assets such as engineering workstations and human-machine interfaces run on standard operating systems.
Dragos also found issues with vulnerability prioritisation. It reported that 25% of ICS-CERT and National Vulnerability Database entries contained incorrect CVSS scores in 2025, and 26% of advisories lacked vendor patches or mitigations. Under Dragos’s risk-based prioritisation model, only 2% of ICS-relevant vulnerabilities were deemed to require immediate action.
In research focused on battery energy storage systems, Dragos identified authentication bypass and command injection flaws, with more than 100 internet-exposed devices detected, including grid-scale power inverters.
The company said organisations with comprehensive OT visibility detected and contained OT ransomware incidents in an average of five days, compared with the broader industry average of 42 days, underscoring the role of monitoring and detection maturity in limiting operational disruption.
You can read the full report here.





