
By Geoff Schomburgk, Vice President for Asia Pacific & Japan, Yubico.
Energy, utilities, oil, gas and telecommunications are increasingly under cyber-attack from nation-states, cybercriminals and hacktivists seeking to cause security and economic disruption. Whilst the 2020 Colonial Pipeline attack was a wake-up call proving just how vulnerable these critical infrastructure companies are to modern cybercriminals due to a single compromised password resulting in a ransomware attack. Have Australian* companies in the critical infrastructure sector done enough to protect themselves in the two years since then?
Widespread regulatory change
The Colonial Pipeline attack was a pivotal point, triggering widespread regulatory change across the globe and in March 2022 the United States Senate approved new cybersecurity legislation that will force critical infrastructure organisations to report cyberattacks and ransomware payments to the Cybersecurity and Infrastructure Security Agency (CISA). Based on evolving intelligence, President Biden recently urged critical infrastructure owners and operators that the Russian Government was exploring options for potential cyberattacks so they must “accelerate efforts to lock their digital doors.”
Whilst, in Australia, the recent revisions to the Security Legislation Amendment (Critical Infrastructure) Act 2021 represent one element of the Government’s response to the growing cyber threats faced by Australian critical infrastructure organisations.
The increasing threats were backed up by the findings in the Australian Cyber Security Centre’s (ACSC) ACSC Annual Cyber Threat Report published in September 2021, which found that cyber-attacks are increasingly severe and frequent at a rate of one attack every eight minutes. Of increasing concern is that the report revealed approximately a quarter of cyber incidents reported to the ACSC in the 2020-21 financial year were associated with Australia’s critical infrastructure or essential services.
In passing the 2021 Security of Critical Infrastructure (SOCI) Act, Australia joins other leading global economies in implementing a regulatory regime to protect its core critical infrastructure assets from cyberattacks. Whereas previously the SOCI Act only covered specific assets in the electricity, gas, water and maritime/ports sectors, the Act now expands the coverage to encompass eleven sectors, including higher education, communications, healthcare, water and sewerage, space technology, food and grocery, defence, data storage and transport.
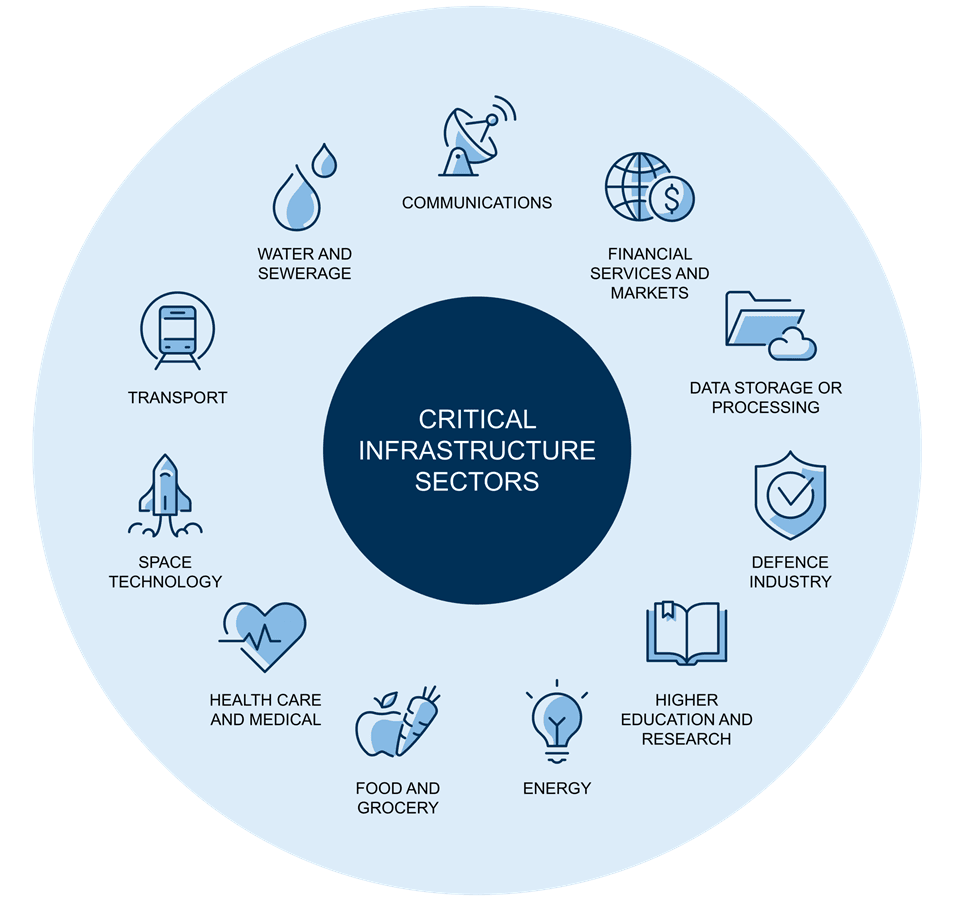
*Source – Gilbert & Tobin
New powers to seize control
The second tranche of the new controversial legislation introduced in February 2022 includes last resort powers for the Australian Signals Directorate empowering them to install and maintain computer software to allow them to take control of serious cyber security incidents that impact the ability of Australia’s critical infrastructure assets to deliver essential services.
Failing to comply with an action direction can result in a penalty of two years imprisonment and/or a fine of $26,640 or $133,200 if the entity is a corporation.
Following consultation, this bill was split in two so that critical aspects of the bill could be progressed whilst other aspects of the bill could be the subject of further debate between government and industry.
The 2021 Bill, which widened the scope of application of the Act, introduced further reporting requirements and provided additional powers to the Commonwealth, was passed and became law on 2 December 2021.
Critical Infrastructure Risk Management Program
On 10 February 2022, the second phase of the SOCI legislation was introduced to Federal Parliament as a Bill, which proposes to introduce obligations on entities to establish a critical infrastructure risk management plan (CIRMP) for critical infrastructure assets increase cyber security obligations for “systems of national significance”. Though currently there are no specifics around how this program will work and no deadline has been given for it to be implemented.
The consultation process with the industry for the proposed introduction of the risk management program is currently underway. The Government has completed its first-phase consultation for the electricity and water and sewerage sectors and consultation with the remaining nine critical sectors is expected to be completed by August 2022.
We all know that prevention is better than a cure but with somewhat vague guidance offered to date to the newer organisations in the critical infrastructure sector, many will do the absolute minimum to achieve compliance to a deadline that keeps shifting.
Mandatory reporting of cyber incidents
The Act introduces new requirements for companies responsible for “critical infrastructure assets” to report cyber security incidents impacting them to the Australian Signals Directorate (ASD). This aims to provide intelligence about cyber security risks to critical infrastructure and to enable proactive and reactive cyber defence strategies.
There are two levels of reporting: critical cyber security incidents and other cyber security incidents. Failing to comply with the reporting obligations can result in a fine of $11,100 per breach, or $55,500 if it is a corporation.
Strong US response
The US government seems to have taken stronger, tangible action by strengthening its legislation with respect to the cybersecurity of its critical infrastructure companies, by implementing mandates for zero trust and phishing resistant Multi-Factor Authentication (MFA).
Legacy authentication is increasing risks for our critical infrastructure
With the gaps in this updated SOCI legislation and the lack of outcomes from the previous Australian Cyber Security Strategy launched in 2020, Australian critical infrastructure organisations are being offered little guidance and few practical actions to implement in their businesses to improve their cybersecurity protection. For instance, an essential element of a Zero Trust strategy was stated by the Australian Government in this initiative as phishing resistant MFA.
Implementing MFA can be a strong first line of defence to protect against modern cyber threats. However, legacy authentication such as usernames and passwords are still widely relied on and can be easily hacked. Whilst mobile-based authentication such as texts, one-time codes, and push notifications are highly susceptible to modern phishing attacks, malware, SIM swaps and man-in-the-middle attacks.
With the average cost of a data breach across the energy sector alone being AU$6.47 million, it’s imperative that Australian critical infrastructure organisations adopt modern phishing-resistant MFA to secure critical IT and OT infrastructures while ensuring compliance with the new legislation.





