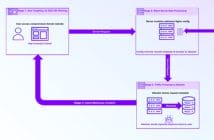
SailPoint has announced additional extensibility functionality to its platform. This allows identity security decisions and workflows that fit within the company’s existing business processes and infrastructure. For example, when an identity change occurs, administrators are automatically notified via a collaboration tool like Slack or Microsoft Teams to take action. There is no longer a need to schedule frequent reviews in other systems to identify and make important identity decisions as workforce access needs evolve to meet business demands.
“By making our SaaS identity platform open and extensible, our customers now have the tools they need to build an identity security solution that supports their unique business environment and requirements,” said Grady Summers, EVP Product, SailPoint. “Our customers are craving the ability to customise and automate in a way that will result in simplicity without a loss in sophistication. We’ve made it foolproof for our customers, easily integrating with virtually any workflow platform, having built native integrations with the industry’s leading iPaaS providers. Identity is the infallible tool for securing an enterprise today and, by embedding it into everyday workflows, identity security can quickly become mainstream to the business, not a hurdle to be overcome.”
With APIs and Event Triggers in the SailPoint Identity Platform, development teams can build integrations designed to support their unique business requirements with access to SDKs, open-source tools, richer documentation, a dedicated forum, and more. Developers will be able to spend less time on the mundane and focus more on what matters: easily integrating identity security into their existing business processes and applications to optimise their overall security. Potential developer customisations made possible include:
- Automate a system to trigger another action, such as sending a notification to deactivate an employee’s badge upon termination;
- Notify an administrator that the SailPoint Identity Platform was able to connect to the source system successfully and was able to collect source accounts;
- Perform quality control, such as continuously checking for separation of duties (SoD) violations.