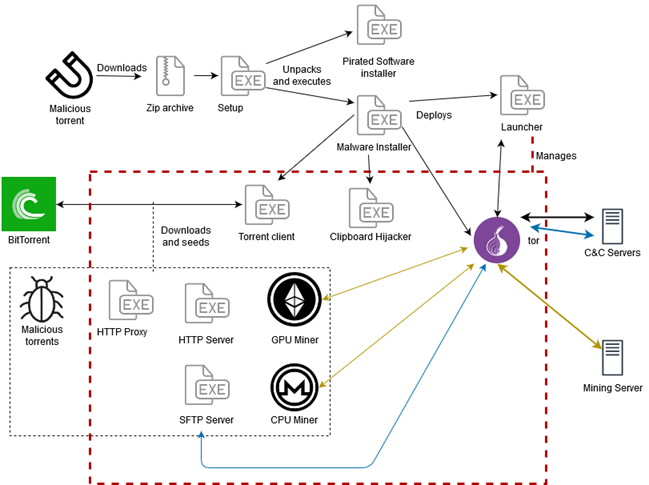
ESET researchers have discovered a previously undocumented trojan malware family that spreads through malicious torrents and that uses multiple tricks to squeeze as many cryptocoins as possible from its victims while staying under the radar. ESET named the threat KryptoCibule, and according to ESET telemetry the malware seems to primarily target users in the Czech Republic and Slovakia.
This malware is a triple threat in regard to cryptocurrencies. It uses the victim’s resources to mine coins, tries to hijack transactions by replacing wallet addresses in the clipboard and exfiltrates cryptocurrency-related files, all while deploying multiple techniques to avoid detection. KryptoCibule makes extensive use of the Tor network and the BitTorrent protocol in its communication infrastructure.
“The malware, as written, employs some legitimate software. Some, such as Tor and the Transmission torrent client, are bundled with the installer; others are downloaded at runtime, including Apache httpd and the Buru SFTP server,” says Matthieu Faou, ESET Researcher who uncovered the new malware family.
ESET has identified multiple versions of KryptoCibule, enabling us to trace its evolution all the way back to December 2018; it remains active. New capabilities have regularly been added to the malware over its lifetime, and it is under constant development.
Most of the victims were in Czech Republic and Slovakia, and this reflects the user base of the site on which the infected torrents are found. Almost all the malicious torrents were available on uloz.to, a popular file sharing site in the two countries. Additionally, KryptoCibule specifically checks for ESET, Avast and AVG endpoint security products; ESET is headquartered in Slovakia, while the other two are owned by Avast, which is headquartered in the Czech Republic.
“KryptoCibule has three components that leverage infected hosts in order to obtain cryptocurrencies: cryptomining, clipboard hijacking and file exfiltration,” explains Faou. “Presumably the malware operators were able to earn more money by stealing wallets and mining cryptocurrencies than what we found in the wallets used by the clipboard hijacking component. Alone, the revenue generated by that component does not seem enough to justify the development effort observed,” he adds.