Researchers at Check Point® Software Technologies Ltd. has shared details of vulnerabilities in Joomla’s mail service, JMail, a popular CMS platform used by hundreds of thousands of organisations around the world.
Check Point Research has found a new campaign from a known threat actor, Alarg53 who is now exploiting a new vulnerability in JMail and is using it to monetise his attack. The Egyptian defacement hacker gained worldwide attention in recent years by hacking Stanford University servers via a WordPress vulnerability for similar purposes. He has managed to hack more than 15,000 sites and has advanced his attacks to include a significant and high-scale backdoor and phishing infrastructure.
JMail enables users to send mail through the platform however without the proper security mechanisms, the mail service can be manipulated to be used for phishing, spam and even implement a backdoor infrastructure within the platform.
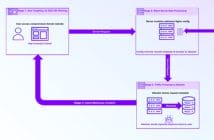
The Attack Flow
Using an old and known object injection Remote Code Execution (RCE), the attacker injects the code to the User-Agent header field in HTTP requests where the PHP code downloads and stores files in a specific path. Once decoded, it is transformed into a PHP code that runs of the victim’s machine.
Once decoded, it is transformed into PHP code that runs on the victim’s machine. In one of the download attempts, Check Point Researchers found an interesting designated path and the URLs to some of the files were dead upon discovery.
Overriding Joomla’s JMail service
The discovered file, HTML file containing PHP code as well as two major sections that serve two functionalities, sending mail and uploading files. Once downloaded and stored, the file actually overrides the current Joomla JMail service.
The file becomes an infrastructure where the attacker can upload files and send mail for his own purposes and in this case for phishing and mail spamming.
JMail Breaker is a significant backdoor and phishing infrastructure established by a known hacker with a strong record. Using an old Joomla object injection vulnerability, the attacker has managed to create an interesting chain that eventually can be leveraged for monetisation through a phishing and spamming infrastructure.
Check Point Research predicts that we will soon see evidence of such spamming methodologies in the future. Check Point customers have IPS protection against Joomla object rejection Remote Command Execution (RCE) and JMailBreaker PHP Web Shell Backdoor.
Follow Check Point via:
Twitter: http://www.twitter.com/checkpointsw
Facebook: https://www.facebook.com/checkpointsoftware
Blog: http://blog.checkpoint.com
YouTube: http://www.youtube.com/user/CPGlobal
LinkedIn: https://www.linkedin.com/company/check-point-software-technologies
About Check Point Software Technologies Ltd.
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from cyber attacks with an industry leading catch rate of malware, ransomware and other types of attacks. Check Point offers a multilevel security architecture that defends enterprises’ cloud, network and mobile device held information, plus the most comprehensive and intuitive one point of control security management system. Check Point protects over 100,000 organisations of all sizes.