
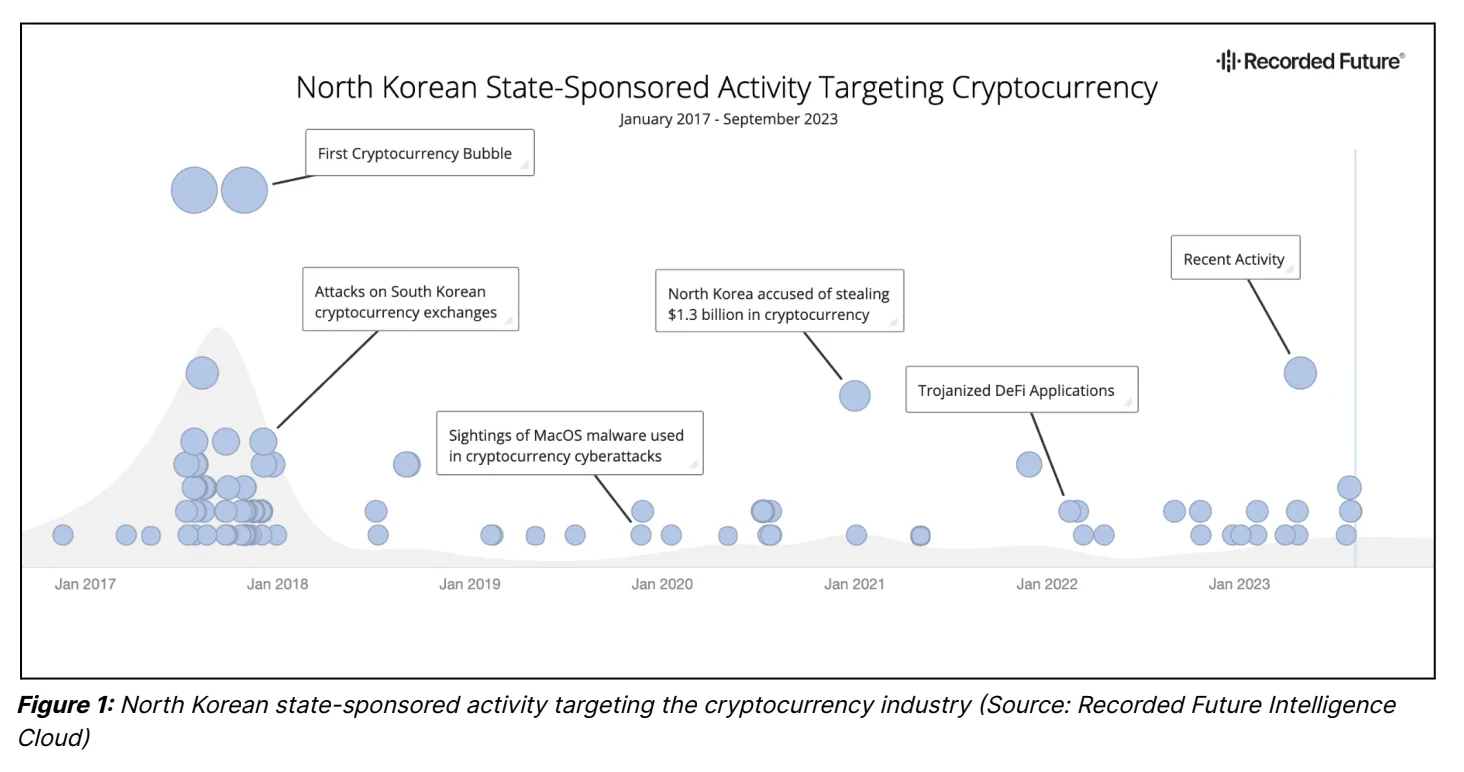
Recorded Future’s threat intelligence unit Insikt Group has revealed the findings of its latest threat analysis – Crypto Country: North Korea’s Targeting of Cryptocurrency – which shows there has been a steady increase in the number of cyberattacks against the cryptocurrency industry globally attributed to North Korea threat actors since at least 2017.
Since the cryptocurrency bubble in 2017 (when the technology reached mainstream), North Korea has stolen over an estimated $3 billion worth of cryptocurrency, with $1.7 billion stolen in 2022 alone, and possibly funding up to 50% of its ballistic missile program.
Even though movement in and out within the “Hermit Kingdom” – referring to North Korea being isolated from the rest of the world – is heavily restricted, the regime’s ruling elite and its highly trained cadre of computer science professionals have privileged access to new resources, technologies, and information. This privileged access equips them with the necessary skills for conducting cyberattacks against the cryptocurrency industry.
The North Korean regime has developed an extensive money-laundering network to facilitate the movement of billions of dollars’ worth of cryptocurrency from when it’s stolen to when it’s converted to fiat currency or used to purchase goods and services for their regime. Their cybercrime operations and money-laundering mirror those of other cybercriminal groups; however, state backing allows North Korean threat actors to scale their operations beyond what is possible for traditional cybercriminals.
Targeting is not limited to cryptocurrency exchanges, with individual users, venture capital firms, and alternative technologies and protocols all having been targeted by North Korean actors. All this activity puts anyone operating in the industry at risk of becoming a potential target of North Korean threat actors and allows the regime to continue operating and funding itself while under international sanctions.
The regime has clearly identified the continued theft of cryptocurrency as a major source of revenue, especially for funding its military and weapons programs. While it is unclear exactly how much of the stolen cryptocurrency ends up directly financing ballistic missile launches, it is clear that both the amount of cryptocurrency being stolen and the amount of missile launches have dramatically increased in recent years.
Absent stronger regulations, cybersecurity requirements, and investments in cybersecurity for cryptocurrency firms, North Korea will almost certainly continue to target the cryptocurrency industry as a source of additional revenue to support the regime.

Impact on individual users, venture capital firms and companies and strategies used by threat actors to go undetected
- Targeting is not limited to cryptocurrency exchanges, with individual users, venture capital firms, and alternative technologies and protocols all having been targeted by North Korean threat actors.
- All of this activity puts anyone operating in the industry at risk of becoming a potential target of North Korean threat actors and allows the regime to continue operating and funding itself while under international sanctions.
- Anyone operating in the cryptocurrency industry — individual users, exchange operators, and financiers with a portfolio of startups — should be aware of the potential to be targeted by North Korean threat actors. Entities operating in the traditional finance space should also be on the lookout for North Korean threat group activities.
- Once cryptocurrency is stolen and converted into fiat currency, North Korean threat actors funnel the funds between different accounts to obscure the source. Oftentimes stolen identities, along with altered photos, are used to bypass anti-money-laundering and know-your-customer (AML/KYC) verification.
- Anyone who is a victim of an intrusion linked to a North Korean threat group may have their personally identifiable information (PII) used to set up accounts to facilitate the laundering of stolen cryptocurrency. As a result, companies operating beyond the cryptocurrency and traditional finance industries should also be on the lookout for North Korean threat group activity and for their data or infrastructuring being used as a launch pad for further intrusions.
A cyber threat analysis (see report for examples of events from 2017 until today)
- A history of crypto currency targeting
- Moving the stolen assets
- Comparison to traditional cybercrime
- Money laundering
Mitigations – 25 tips and recommendations including:
- Enabling MFA for software wallets and transactions with a hardware device such as YubiKey.
- Ensuing requested transactions are legitimate and validate any airdrops or other free cryptocurrency or NFT promotions.
- Using hardware wallets which can be much more secure than “hot wallets” like MetaMask, which are always connected to the internet.
- Only using trustworthy dApps (Decentralized Applications) and verify smart contract addresses to confirm their authenticity and integrity.
- Resisting pressure tactics. Scams often induce a sense of urgency to pressure victims into impulse actions, and cryptocurrency-drainer phishing scams are no exception.
- Transferring existing cryptocurrency investments into stablecoins that are backed by governments or pegged to a fiat currency to insulate them from market fluctuations.
- Attempting to verify any links posted within the official Discord or other P2P communication platforms used by NFT creators and sponsors.
- Using anti-cryptomining extensions, such as the Google extensions minerBlock, NoMiner, and Anti-Miner, to block cryptominers across the web and use Ad-Blockers that can detect and block malicious cryptomining code. Furthermore, organizations should reduce the exposure of control devices to ensure they remain inaccessible from the internet.
You can read the full report here.





