Netskope Threat Labs has identified a new phishing campaign using fake video conference invitations to deliver remote access tools into corporate environments.
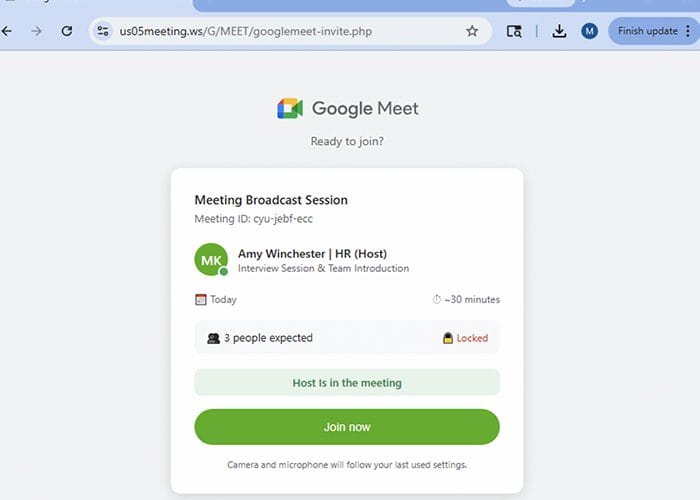
According to research, the campaign targets enterprise users with spoofed meeting invites for widely used platforms including Zoom, Microsoft Teams and Google Meet. Victims are prompted to install what is presented as a mandatory software update before joining the meeting.
The phishing pages are designed to closely resemble legitimate conferencing portals and include visual elements such as simulated participants appearing to join the call in real time. Once users attempt to proceed, they are prompted to download and execute an update package.
Instead of a legitimate update, the download contains a remote monitoring and management (RMM) tool. While RMM software is commonly used by IT and security teams for legitimate remote administration, it can also be abused by attackers to gain persistent access to compromised systems.
Because many RMM tools are pre-approved within enterprise environments, their deployment may not immediately trigger signature-based security controls. This can allow attackers to establish administrative-level access while avoiding early detection.
Netskope researchers said the campaign highlights a broader trend of threat actors leveraging trusted enterprise tools and workflows to bypass traditional security measures and embed themselves within corporate networks.